A computer scientist has uncovered weaknesses in the application verification service Google recently rolled out to help users detect malicious apps on their Android smartphones and tablets.
"By introducing this new app verification service in Android 4.2, Google has shown its commitment to continuously improve security on Android," Xuxian Jiang, a professor of computer science at North Carolina State University, wrote in a brief report published Monday. "However, based on our evaluation results, we feel this service is still nascent and there exists room for improvement."
Jiang exposed Nexus 10 tablets running the Jelly Bean version of Android to 1,260 samples of malicious apps and found that the built-in scanner detected only 193 of them. That indicates a detection rate of just 15.32 percent.
Jiang also found the performance of Google's app verification lagged well behind the performance of 10 representative antivirus apps offered by third-party companies such as Avast, Symantec, and Kaspersky Lab. He did this by picking a pseudo random code sample from each of 49 malware families. Overall, the detection rates of the AV packages was 51 percent to 100 percent, compared with 20 percent for the Google service, which is included with the Google Play app. The scanning service, which examines apps downloaded from Google Play as well as alternate sources, is optional, although it's on by default. Jiang's report didn't rank the specific AV apps or list the detection rates for each one by name.
A chief reason the app verification service misses so much malware is its reliance on cryptographic hash signatures to identify apps known to be malicious.
"This mechanism is fragile and can be easily bypassed," Jiang wrote. "It is already known that attackers can change with ease the checksums of existing malware (e.g., by repackaging or mutating it). To be more effective, additional information about the app may need to be collected. However, how to determine the extra information for collection is still largely unknown—especially given user privacy concerns."
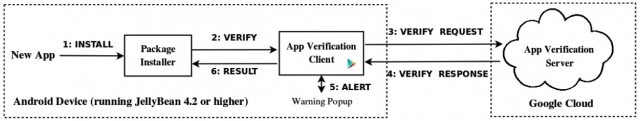
Jiang also faulted the service for hosting the scanner solely in the cloud rather than using some sort of client-side solution.
"Unfortunately, it is not realistic to assume that the server side has all existing malware samples (especially with limited information such as app checksums and package names)," he wrote. "From another perspective, the client side, in the current implementation, does not have any detection capability, which suggests possible opportunity for enhancement. However, due to the limited processing and communication power on mobile devices, we need to strike a delicate balance on how much detection capability can and should be offloaded."
Jiang said VirusTotal, the free app-scanning website recently acquired by Google, also outperformed the app verification service. He said the service is likely to improve if it integrates VirusTotal.
Jiang's findings are sure to be hailed by makers of standalone apps that detect Android malware, like Lookout. On Friday, the company said an update it had pushed out mistakenly flagged legitimate apps, including one offered by Movie service Fandango, as malicious. The mistake was detected and fixed about an hour later.
Listing image by amboo who?
reader comments
120