A Google-backed file sharing service has been discovered spreading malware to thousands of Windows and Android users.
An investigation by security company Eset has revealed that Xunlei has been spreading malware named “Win32/Kankan” to Windows and Android users, signed with the company’s security certificate.
The malware is classed as a Trojan, and only affected Chinese users, according to Eset.
“The company officially admitted during a press conference that some of its employees have used company resources to create and distribute this program. The degree to which Xunlei Networking Technologies is implicated is hard to tell from the outside,” said Joan Calvet from Eset in a blog post.
The Xunlei software is very popular in China and has about 30% of world BitTorrent users, making it the most used BitTorrent client for the service, which allows peer-to-peer file sharing. The BitTorrent protocol breaks each file to be shared into small chunks and sends them across the internet between computers. Parts of the complete file can be hosted on many different computers, and the whole reconstructed by pulling the parts from different machines.
Effectively evading detection
It is unclear how the malware, which was specifically programmed to avoid detection by security software and analysts, was initially spread.
A “dropper” program named “INPEnhSetup.exe” posed as a Windows installer, which once activated contacted a server across the internet – a domain owned and operated by Xunlei - and “dropped” or installed three further malicious programs onto the system.
One of the programs, a plugin for the Microsoft Office applications Word, Excel and PowerPoint, then installed itself within the Windows Registry, ensuring that it was loaded every time an Office application is run.
When run, the Office plugin scanned the computer for analysis tools such as the Windows task manager, and quickly shut down if one was found running on the system, effectively evading detection by the computer user or a security analyst.
If the program failed to detect any running computer analysis tools, it began sending user information such as the version of Windows being used to a remote server.
Silently installing applications onto Android phones
The malware also included an updater that automatically checked a server for new versions of the programs, installing updates when they became available.
Another application installed alongside the Office plugin silently installed applications onto Android phones that were connected to the infected computer.
Using the USB connection, the “installphoneapp” installed applications, including three separate Chinese app stores, and a phone call app that claimed to offer cheap phone calls.
“Overall, the motivation behind the installation of these particular mobile applications remains unknown,” said Calvet.
The applications were only installed if the Android phone connected had a security setting disabled, which enables developer actions over USB on the phone – something often required for Android software modifications and operating system customisation, as well as by certain Android backup programs.
“We’ve seen desktop malware attempt to install Android malware before, but not through the application of Android’s ADB. Pushing it to Android phones like that is novel,” said Rik Ferguson vice president of security research at Trend Micro.
A lot of mobile malware is specific to China
The focus on China meant that the risk of the Trojan spreading was low, according to Ferguson.
“Of course, the risk of Android malware infection is massively increased by rooting, which this malware example partly targeted, because you are specifically disabling crucial built-in security services,” he said.
More rooted phones exist in China, mainly due to the restrictions on apps and services, which require users to circumvent blocks to get access to many of the applications freely available in the UK and the US.
“We see a lot of mobile malware that is specific to China, like a lot of other malware,” explained Ferguson. “For example, we see malware targeted at stealing virtual goods in gaming environments only in China.”
According to data collected by Trend Micro, there are 1.15m malicious or high-risk Android apps currently circulating as of 12 October, which is significantly higher than estimates based on malware growth seen in 2012, showing that the problem is increasing dramatically.
Pushing the installer out to infected machines
It remains unclear whether Xunlei’s BitTorrent client was used to spread the malware. Since August, Xunlei made available an uninstaller application, which users could download and remove the problem manually.
Using the company owned and operated servers, which the malware automatically contacted, Xunlei also pushed out the installer to infected machines.
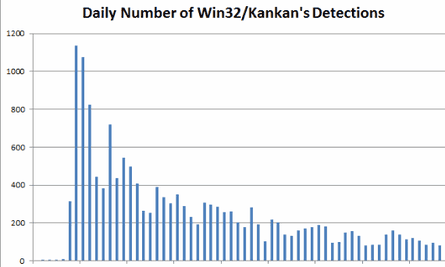
According to Eset’s data, the daily number of infections has dropped significantly since Xunlei’s remedial actions.
In August, Windows malware was found lurking within the KFC app for Android.




Comments (…)
Sign in or create your Guardian account to join the discussion