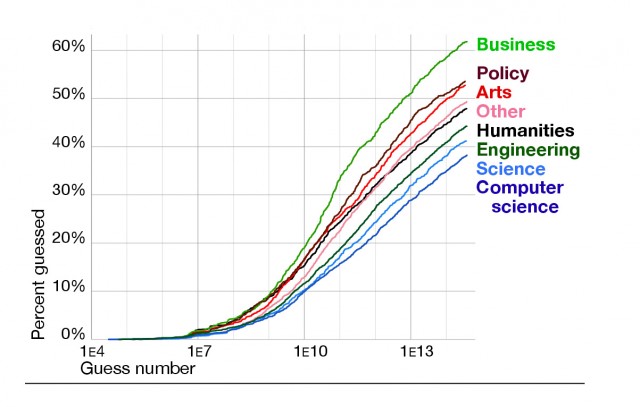
If you're a student or teacher in a computer science school of a big college, chances are good that you pick stronger passwords than your peers in the arts school. In turn, the arts students usually pick better passwords than those in the business school, according to research presented this week.
The landmark study is among the first to analyze the plaintext passwords that a sizable population of users choose to safeguard high-value accounts. The researchers examined the passwords of 25,000 faculty, staff, and students at Carnegie Mellon University used to access grades, e-mail, financial transcripts, and other sensitive data. The researchers then analyzed how guessable the passwords would be during an offline attack, such as those done after hackers break into a website and steal its database of cryptographically hashed login credentials. By subjecting the CMU passwords to a cracking algorithm with a complex password policy, the researchers found striking differences in the quality of the passwords chosen by various subgroups within the university population.
For instance, people associated with CMU's computer science and technology schools chose passwords that were more than 1.8 times stronger than those used by people in the business school. In between these two groups were people associated with the art school. Statistically speaking, passwords picked by computer science and technology users were only 68 percent as likely to be guessed as arts users and only 55 percent as likely to be cracked as people in the business school. Stated differently, the number of attempts required to successfully guess 100 arts school passwords in the typical offline crack would yield passwords for 124 people in the business school and 68 people in the computer science school.
The research paper, titled Measuring Password Guessability for an Entire University (PDF) is significant because it's among the few that have studied a statistically significant sample of passwords used for high-value accounts. By comparison, the findings of many previous studies have been less reliable because they analyzed smaller numbers of passwords, passwords taken from real-world database breaches, or passwords created for one-off accounts set up for research purposes.
The paper, which was presented in Berlin at this week's 20th ACM Conference on Computer and Communications Security, is also important because its findings may one day help people who secure computer networks and websites provide better password guidance and policies. As Ars has reported in a series of articles over the past 18 months, advances in hardware, software, and experience are increasingly giving passwords crackers the upper hand. This advantage often carries over even when users resort to long passphrases."This kind of experiment can't tell us anything about why this effect is going on, just that it is," Michelle L. Mazurek, one of the researchers who wrote the paper, told Ars. (Disclosure: Mazurek is married to Ars Senior Gaming Editor Kyle Orland.) She continued:
So it could mean that business school users don't know how to make stronger passwords (that is, they are trying but aren't as good at it), or it could mean they are making less effort or care less about protecting their accounts, or something else entirely. I think in practice it means that some extra education may be needed either to help those users learn to make stronger passwords or to give them more motivation to make stronger passwords. In general I think if you are a sysadmin trying to bring up the strength of passwords across the organization, it gives you some sense of where to focus your efforts (at least in populations that somewhat resemble the CMU population).
Perhaps not surprisingly, the researchers also found that length and other password characteristics are strongly correlated to strength. With the addition of each lowercase letter or digit, for instance, a password is 70 percent as likely to be guessed. Adding special symbols or uppercase letters made passwords even stronger, reducing the likelihood of guessing to 56 percent and 46 percent respectively. The researchers go into additional detail:
Placing digits and symbols anywhere but at the end, which is the baseline for the regression, is also correlated with stronger passwords. Multiple characters spread out in more than one location are associated with the strongest passwords—only 20% and 30% as likely to be guessed as passwords with digits and symbols, respectively, at the end. Placing uppercase characters at the beginning instead of at the end of a password is associated with much weaker passwords: 88% more likely to be guessed.
The researchers also found that men in the study used slightly stronger passwords than women. Men's passwords were 92 percent as likely as women's to be guessed, meaning on average the number of attempts required to successfully guess 100 women's passwords would yield 92 passwords belonging to men.
The research also showed that people who pick stronger passwords have higher rates of failed login attempts and that users who report annoyance with CMU's stringent password policy picked weaker passcodes.
Listing image by Dev.Arka
reader comments
84