![Ancient Linux servers: The blighted slum houses of the Internet [Updated]](https://cdn.arstechnica.net/wp-content/uploads/2014/03/crack-house.jpg)
Update on March 24 at 7:03 California time:The Cisco blog post has been updated to change a key finding Ars reported in the following post. Contrary to Cisco's earlier reporting, the update says not all the servers compromised in the attack were running Linux version 2.6. "We have not identified the initial exploit vector for the stage zero URIs," the update stated. "It was not our intention to conflate our anecdotal observations with the technical facts provided in the listed URIs or other demonstrable data, and the below strike through annotations reflect that. We also want to thank the community for the timely feedback."
Earlier this week, Ars reported on attacks exploiting an extremely critical vulnerability in the PHP scripting language almost two years after the bug came to light. By going 22 months without installing crucial patches, the responsible administrators were menacing the entire Internet, in much the same way as the owner of a blighted building might contribute to increased urban decay or neighborhood crime.
Now comes word of a new mass compromise that preys on even more neglected Web severs, some running versions of the Linux operating system kernel first released in 2007. According to a blog post published late Thursday by researchers from Cisco, the people behind the attack appear to have identified a vulnerability that has since been patched in later Linux releases that allows them to dish malicious content to unsuspecting people who visit the site. The quick-spreading compromise took over 400 hosts per day on Monday and Tuesday, and so far, Cisco has counted more than 2,700 distinct URLs that are under the control of the attackers."This large-scale compromise of an aging operating system highlights the risks posed by leaving such systems in operation," Martin Lee, a threat intelligence technical lead in Cisco's Security Intelligence Operations group, wrote. "Systems that are unmaintained or unsupported are no longer patched with security updates. When attackers discover a vulnerability in the system, they can exploit it at their whim without fear of it being remedied."
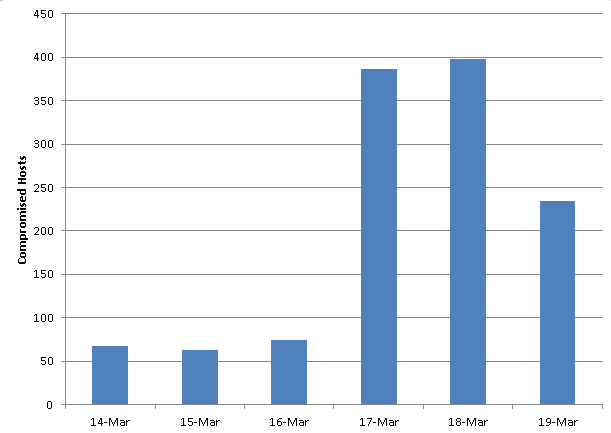
The mass infection works against servers running version 2.6 of the Linux operating system kernel, some using releases from 2007 or earlier, Lee said. The attacks cause otherwise legitimate websites to serve fraudulent pages and pay-per-view ads to visitors. Lee said there's also anecdotal evidence that visitors are exposed to attacks that install malware on their computers. Underscoring the effect the infected servers are having on the Internet at large, one in 15 customers using a Cisco safe-browsing cloud service have had at least one user exposed to the attacks. The end-user attacks work in a two-stage process that mixes JavaScript code from multiple servers in a way that can ultimately become harmful.
Some antivirus products are flagging the attacks as those used by the Blackhole exploit kit, but Lee said the detection is probably erroneous. It's more likely, he said, that the attack code being served to end users is related to a malware campaign uncovered in January by researchers from security firm Sucuri. Infected servers are found all over the world, with large concentrations in Germany and the US.
Cisco's post is a potent reminder that people running any unpatched operating system put the entire Internet at risk. Given the likelihood that a significant percentage of the infected sites are run by hobbyists or mom-and-pop operations with modest resources and little security expertise, there's no clear antidote to the rash of outdated machines. One possibility is for Web hosts to begin mandating a set of criteria for the servers permitted to operate on their networks. Such a solution is probably unworkable, since it would likely result in increased workloads and strained customer relations for the hosting companies that take on the challenge. Until a fix comes along, it's "end user beware."
"Large numbers of vulnerable unpatched systems on the Internet are tempting targets for attackers," Lee wrote. "Such systems can be used as disposable one-shot platforms for launching attacks. This makes it all the more important that aging systems are properly maintained and protected."
reader comments
104