How to use the NMAP Security Scanner on Linux
Nmap is a free and open-source network discovery and security auditing utility that is widely used in the Linux users community as it is simple to use yet very powerful. Nmap works by sending data packets on a specific target (by IP) and by interpreting the incoming packets to determine what posts are open/closed, what services are running on the scanned system, whether firewalls or filters are set up and enabled, and finally what operating system is running. Those abilities are used for a wide variety of reasons and howtoforge.com is not encouraging nor suggesting the use of Nmap for malicious purposes.
Install Nmap
First of all, you should get the “nmap” package installed in your system.
On CentOS
yum install nmap
On Debian
apt-get install nmap
On Ubuntu
sudo apt-get install nmap
Using the Nmap security scanner
Then you may run the command “nmap” on a terminal, accompanied by the target's IP or website address and the various available parameters. To get an overview of all the parameters that nmap can be used with, use the “nmap –help” command.
In order to introduce you to nmap, I will give some usage examples together with a brief explanation that will hopefully enable the reader to modify each command to his/her needs.
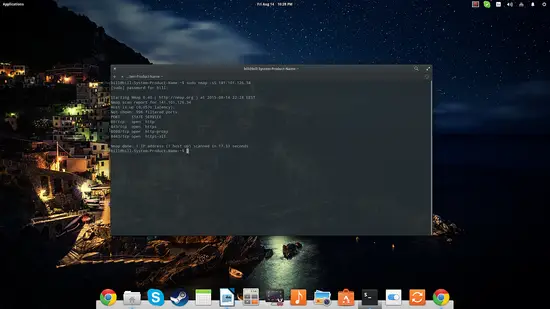
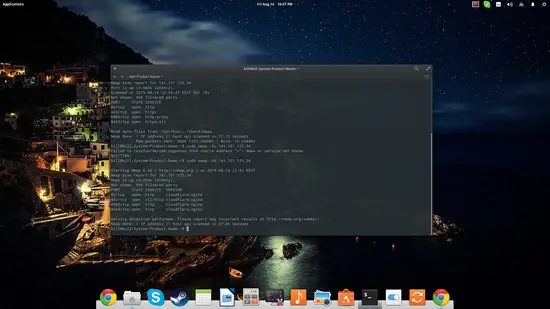
sudo nmap -sS [IP address] or [website address]
This is a basic command that can be used to quickly check if a website is up (in that case, I used the howtoforge.com IP) without creating any “loggable” interaction with the target server. Note that there are four open ports shown as well.
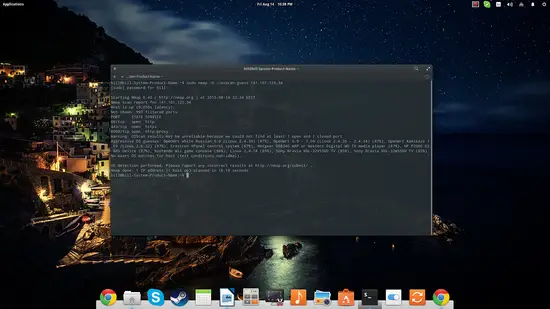
sudo nmap -O --osscan-guess [IP address] or [website address]
This command instructs nmap to try to guess what operating system is run on the target system. If all ports are filtered (which is the case in the screenshot), this “guessing” command will be the best option, but the results can't be considered reliable. The percentage numbers are giving the idea of uncertainty.
sudo nmap -vv [IP address] or [website address]
This is a ping scan command that is helpful when wanting to check the open ports of a target.
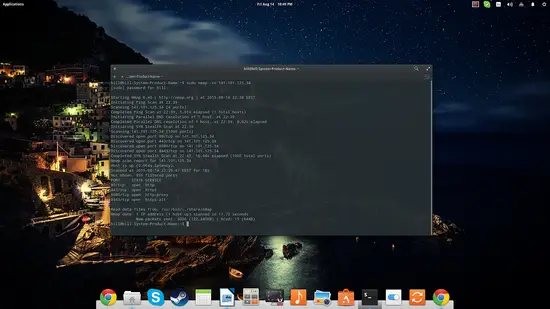
sudo nmap -sV [IP address] or [website address]
This command allows the user to check the services run on the target. Note that the “cloudflare-ngnix” information was added next to the services of the open ports.
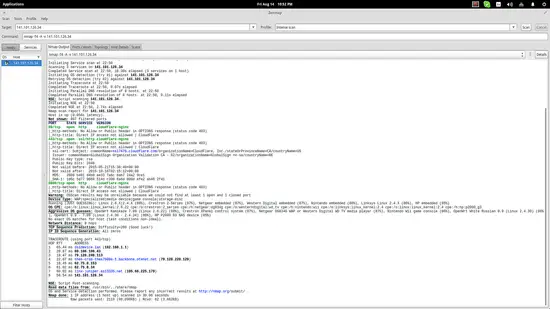
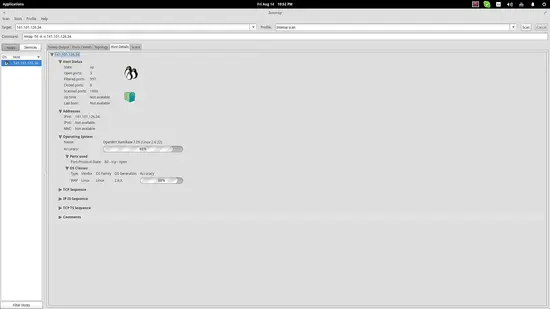
Zenmap - A GUI for Nmap
All the above is good and you can dive deeper trying out various options and see what you can learn about a target, but for those that want a more user-friendly approach, they should install the “zenmap” package that is a GUI tool for Nmap. More information on zenmap can be found here.
Besides the fact that Zenmap offers convenient boxes to insert your target's IP (or website address) and outputs results in a more eye-pleasing way and with proper highlighting, its main advantage is the fact that it offers pre-set Nmap commands that you can quickly select and run. Moreover, the software offers a test comparison tool, a topology plotter, and the ability to save scans for administrator review and evaluation.