
Getting a Linux server hacked and made part of a botnet is easier than some people may think. As two unrelated blog posts published in the past week demonstrate, running a vulnerable piece of software is often all that's required.
Witness, for example, a critical vulnerability disclosed earlier this year in Elasticsearch, an open source server application for searching large amounts of data. In February, the company that maintains it warned it contained a vulnerability that allowed hackers to execute commands on the server running it. Within a month, a hacking forum catering to Chinese speakers provided all the source code and tutorials needed for people with only moderate technical skills to fully identify and exploit susceptible servers.
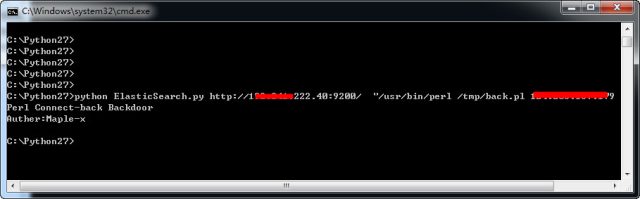
A post published Tuesday by security firm Recorded Future deconstructs that hacker forum from last March. It showed how to scan search services such as Shodan and ZoomEye to find vulnerable machines. It includes an attack script written in Python that was used to exploit one of them and a separate Perl script used to make the newly compromised machine part of a botnet of other zombie servers. It also included screenshots showing the script being used against the server. The tutorial underscores the growing ease of hacking production servers and the risk of being complacent about patching.
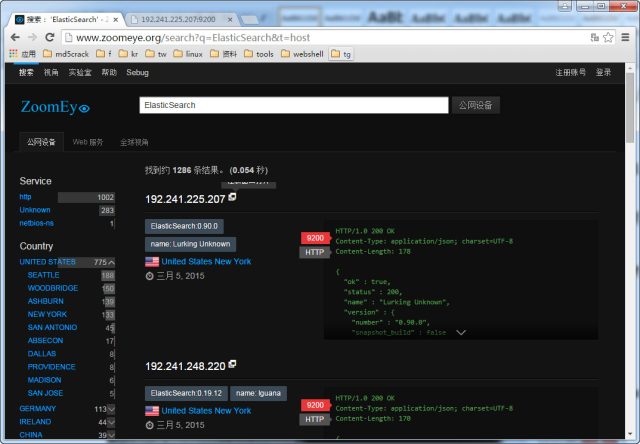
"These Chinese actors are jumping quickly with a ready-to-go kit," Levi Gundert vice president of threat research at Recorded Future, told Ars. "It seems that there's a significant amount of Chinese chatter when a new remote vulnerability is announced for a platform with real market share. The scanning seems to start almost immediately for vulnerable instances."
Gundert said that the hackers in the forum were using the servers to execute distributed denial-of-service attacks. To his surprise, they didn't appear to be interested in the data stored on the hacked servers themselves. Of course, copycat hackers could easily modify or expand the code to suit their own purposes.
A separate blog post published last week also underscores the ease of getting hacked when running the wrong Linux application. On November 3, a weakness was disclosed in Redis, another open source application for data. Within a week, someone had exploited it on a server the author maintained and was using it in a DDoS botnet. The author had forgotten Redis was installed because, when experimenting with an application that relied on it, he had installed it using both the Linux package manager and a direct download from the Internet.
"Install things through the package manager when possible," the blog post concludes. "This makes it easier to uninstall the software cleanly." It also went on to impart several other lessons, including the importance of running apps with as few administrative privileges as possible.The larger lesson is that the growing user base of Linux and the large number of applications that run on it are making it easier and more profitable to carry out hack attacks that were once associated only with Windows PCs. Now, more than ever, vigilant patching and attention to security are a must.
reader comments
54