HTTPOXY Vulnerability: How to protect and test your web server
The HTTPOXY vulnerability which has been found recently is a vulnerability that affects applications that run in cgi or cgi-like environments. This means that the issue affects almost all web servers including Apache and Nginx and also most PHP applications. Even the mod_php mode on apache is affected.
This tutorial will show you how to protect your web server from HTTPOXY. It contains sections for the most used Linux Distributions CentOS + RHEL, Debian, and Ubuntu. The steps can be applied to other Linux distributions as well, but the paths to the configuration files might differ.
A detailed description of the HTTPOXY vulnerability can be found on this website https://httpoxy.org/.
The steps described in this tutorial are compatible with the ISPConfig perfect server tutorials.
1 How does HTTPOXY affect my server?
HTTPOXY affects clients that honor the HTTP_PROXY variable and use it for their proxy configuration and server side applications which use HTTP_PROXY as real or emulated variable in their environment. The result of an attack can be traffic that gets proxied by the web application to a target system chosen by the attacker or the application opens outgoing connections to other systems. The vulnerability is easily remotely exploitable and servers can be scanned for it, so it is highly recommended to take actions to close it on your server.
1.1 General solution
The recommended solution at the moment is to unset or filter the HTTP_PROXY header variable. This is done in apache with the mod_headers module and this configuration statement:
RequestHeader unset Proxy early
On Nginx you can use this line to unset the HTTP_PROXY variable.
fastcgi_param HTTP_PROXY "";
The next chapter describes the detailed procedure for different Linux Distributions.
2 Debian
This chapter describes the configuration to protect Apache and Nginx on Debian 8 (Jessie) and Debian 7 (Wheezy) servers against HTTPOXY. The next steps assume that you are logged in as root user on the shell. If you are logged in under a different user, then use the su command (or sudo if you configured sudo) to become the root user.
2.2 Debian 8 (Jessie) with Apache
Enable the apache headers module
a2enmod headers
Add a global configuration file /etc/apache2/conf-available/httpoxy.conf. I will use the nano editor here:
nano /etc/apache2/conf-available/httpoxy.conf
and paste the following content to that file:
<IfModule mod_headers.c>
RequestHeader unset Proxy early
</IfModule>
Save the file. Then enable it in the configuration with the a2enconf command and restart apache.
a2enconf httpoxy
service apache2 restart
2.2 Debian 7 (Wheezy) with Apache
Enable the apache headers module:
a2enmod headers
Add a global configuration file /etc/apache2/conf.d/httpoxy.conf. I will use the nano editor here:
nano /etc/apache2/conf.d/httpoxy.conf
and paste the following content to that file:
<IfModule mod_headers.c>
RequestHeader unset Proxy early
</IfModule>
Save the file. Then restart apache.
service apache2 restart
2.3 Debian with Nginx
The following command will add a fastcgi_param that sets the HTTP_PROXY variable to an empty string to the /etc/nginx/fastcgi_params file.
echo 'fastcgi_param HTTP_PROXY "";' >> /etc/nginx/fastcgi_params
Then restart nginx to apply the configuration change.
service nginx restart
3 Ubuntu
This chapter describes the configuration to protect Apache and Nginx on Ubuntu 14.04 - 16.04 servers against HTTPOXY.
3.1 Ubuntu with Apache
Enable the apache headers module.
sudo a2enmod headers
Add a global configuration file /etc/apache2/conf-available/httpoxy.conf. I will use the nano editor here:
sudo nano /etc/apache2/conf-available/httpoxy.conf
and paste the following content to that file:
<IfModule mod_headers.c>
RequestHeader unset Proxy early
</IfModule>
Save the file. Then enable it in the configuration with the a2enconf command and restart apache.
sudo a2enconf httpoxy
sudo service apache2 restart
3.2 Ubuntu with Nginx
The steps to protect Ubuntu against HTTPOXY are similar to the ones for Debian. We just have to ensure to run the commands with sudo. This echo command will add a fastcgi_param line that sets the HTTP_PROXY variable as an empty string. The file /etc/nginx/fastcgi_params is included into the default @PHP and cgi-bin sections of the nginx vhost files and also in vhosts that get created by ISPConfig. If you added custom vhosts, then checj that they contain "include /etc/nginx/fastcgi_params;" in the config sections for php and other cgi or fastcgi connectors.
Run the following command to add the empty HTTP_PROXY variable.
sudo echo 'fastcgi_param HTTP_PROXY "";' >> /etc/nginx/fastcgi_params
Then restart Nginx to apply the configuration change.
sudo service nginx restart
4 CentOS, RHEL and Fedora
This chapter describes the configuration to protect Apache and Nginx on CentOS servers against HTTPOXY. The same steps should work for Fedora servers as well. Login as root user on the shell before you proceed with the commands below.
4.1 Apache
The Apache (httpd) configuration file on CentOS is /etc/httpd/conf/httpd.conf. I will add the apache header rule at the end of the httpd.conf file with this command:
echo "RequestHeader unset Proxy early" >> /etc/httpd/conf/httpd.conf
Then restart httpd to apply the configuration change.
service httpd restart
4.2 Nginx
The Nginx web server on CentOS includes the fastcgi_params into the PHP and CGI section of the default vhost, so we can add the rule to set the empty HTTP_PROXY variable there. Run this command to add the empty HTTP_PROXY variable.
echo 'fastcgi_param HTTP_PROXY "";' >> /etc/nginx/fastcgi_params
Then restart nginx to apply the configuration change.
service nginx restart
5 Test
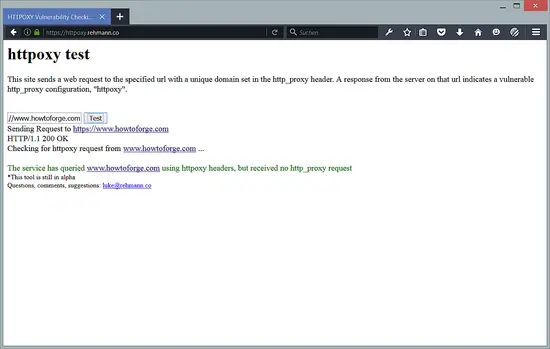
Finally, you should test if your server is safe now. Luke Rehman has developed a nice online testing tool which can be found here: https://httpoxy.rehmann.co/
Enter the URL to your server or website in the tool and click on the "test" button.
Here is the result for howtoforge.com. As you can see, our website is safe.
6 Links
- The HTTPOXY Website https://httpoxy.org/
- Thanks to Jesse for the Debian 8 recipe.