Keylogger found on thousands of WordPress-based sites, stealing every keypress as you type
A new report from researchers at Sucuri reveals that websites are once again being found infected by cryptomining code – stealing the resources of visiting computers to mine for the Monero cryptocurrency.
Many web surfers almost certainly don’t realise that the reason that their laptop’s fan is running at full blast is because the website they are viewing is tied up with the complex number-crunching necessary to earn the digital currency.
But, in a twist, this particular attack isn’t just interested in mining Monero. While the website’s front-end is digging for cryptocurrencies, the back-end is secretly hosting a keylogger designed to steal unsuspecting users’ login credentials.
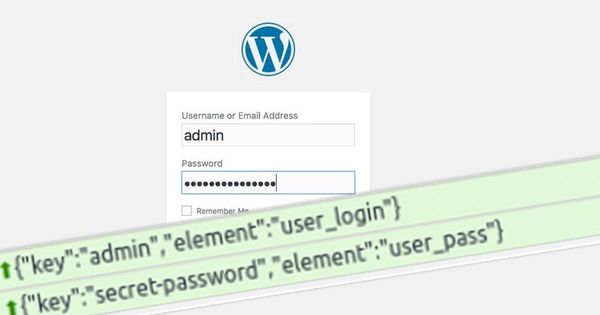
With the keylogger in place, any information entered on any of the affected websites’ web forms will be surreptitiously sent to the hackers.
And yes, that includes the site’s login form.

As if that wasn’t bad enough, what is typed in the forms is sent to the hackers even before the user has clicked on the “log in” button.

If a hacker manages to steal the credentials of the site’s administrator they won’t need to rely upon a vulnerability to break into the site in future, they can just login without a care in the world. (And yes, that’s another reason why WordPress accounts should be defended with two-factor authentication).
As Bleeping Computer reports, there are at least 2,000 WordPress sites infected with the keylogger. This is in addition to earlier related attacks which were affecting near 5,500 WordPress sites last month.
We’ve said it before, and we’ll no doubt say it again. And again.
If your website is powered by the self-hosted edition of WordPress, it’s essential that you keep both it, and any third-party plugins, updated.
Self-hosting your WordPress site is attractive in many ways, but you have to acknowledge that security is now your responsibility (or find yourself a managed wordpress host who is prepared to take it on for you). New vulnerabilities are found in the software and its many thousands of third-party plugins all the time.
In short, if you don’t know what you’re doing, there’s a chance that your WordPress-running website has security holes which a malicious hacker could exploit. Such security weaknesses could potentially damage your brand, scam your website visitors, and help online criminals to make their fortune.
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
Start Cyber Resilience and Don’t Be an April Fool This Spring and Beyond
April 01, 2024
Spam trends of the week: Cybercrooks phish for QuickBooks, American Express and banking accounts
November 28, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks







