How to Install Passbolt Self-Hosted Password Manager on CentOS 8
Passbolt is an open-source password manager that allows you to store and share your password securely. It is designed for small and medium-sized organizations to store and share the login credential between team members. It is self-hosted and available in both community and subscription-based editions.
In this tutorial, we will show you how to install Passbolt password manager with Nginx and Let's Encrypt SSL on CentOS 8.
Prerequisites
- A server running CentOS 8.
- A valid domain name pointed with your server IP.
- A root password is configured on your server.
Install LEMP Server
First, install Nginx and MariaDB database server using the following command:
dnf install nginx mariadb-server -y
Next, you will need to install the latest version of PHP and other required PHP extensions in your server. By default, the latest version of PHP is not available in the CentOS default repo. So you will need to add EPEL and REMI repo to your system.
You can add both repos with the following command:
dnf install epel-release -y
dnf install https://rpms.remirepo.net/enterprise/remi-release-8.rpm -y
Next, disable the default PHP repo and enable the REMI repo with the following command:
dnf module reset php
dnf module enable php:remi-7.4
Next, install PHP with other required dependencies by running the following command:
dnf install php php-fpm php-intl php-gd php-mysqli php-json php-pear php-devel php-mbstring php-fpm git make unzip -y
After installing all the packages, you will need to edit the PHP-FPM configuration file and change the user and group to Nginx.
nano /etc/php-fpm.d/www.conf
Change the following lines:
user = nginx group = nginx
Save and close the file then change the ownership of the session directory:
chgrp nginx /var/lib/php/session
Next, start the Nginx, MariaDB and PHP-FPM service and enable them to start at system reboot with the following command:
systemctl start mariadb nginx php-fpm
systemctl enable mariadb nginx php-fpm
Next, you will need to install the GNUPG extension to your system. You can install it by running the following commands:
dnf config-manager --set-enabled powertools
dnf install gpgme-devel
pecl install gnupg
echo "extension=gnupg.so" > /etc/php.d/gnupg.ini
Next, restart the PHP-FPM service to apply the changes:
systemctl restart php-fpm
Install Composer
Composer is a dependency manager for PHP. You will need to install it in your system.
First, download the Composer setup file with the following command:
php -r "copy('https://getcomposer.org/installer', 'composer-setup.php');"
Next, install the Composer with the following command:
php composer-setup.php --install-dir=/usr/local/bin --filename=composer
You should get the following output:
All settings correct for using Composer Downloading... Composer (version 2.0.11) successfully installed to: /usr/local/bin/composer Use it: php /usr/local/bin/composer
Next, verify the Composer version with the following command:
composer -V
You should get the following output:
Composer version 2.0.11 2021-02-24 14:57:23
Create a Database
Next, you will need to create a database and user for Passbolt.
First, connect to MariaDB with the following command:
mysql
Once connected, create a database and user with the following command:
MariaDB [(none)]> CREATE DATABASE passbolt DEFAULT CHARACTER SET utf8mb4 COLLATE utf8mb4_unicode_ci;
MariaDB [(none)]> GRANT ALL ON passbolt.* TO 'passbolt'@'localhost' IDENTIFIED BY 'password';
Next, flush the privileges and exit from the MariaDB with the following command:
MariaDB [(none)]> FLUSH PRIVILEGES;
MariaDB [(none)]> EXIT;
Once you are finished, you can proceed to the next step.
Install and Configure Passbolt
First, change the directory to Nginx web root directory and download the latest version of Passbolt with the following command:
cd /var/www
git clone https://github.com/passbolt/passbolt_api.git passbolt
Once the download is completed, change the directory to passbolt and install all required dependencies with the following command:
cd passbolt
composer install --no-dev
Next, you will need to install haveged to generate the GPG key. First, install the haveged with the following command:
dnf install haveged
Next, start the haveged service with the following command:
systemctl start haveged
Next, generate the GPG key with the following command:
gpg --full-generate-key
Answer all questions carefuly. Leave the password field blank when ask to set a password:
gpg (GnuPG) 2.2.9; Copyright (C) 2018 Free Software Foundation, Inc.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
gpg: directory '/root/.gnupg' created
gpg: keybox '/root/.gnupg/pubring.kbx' created
Please select what kind of key you want:
(1) RSA and RSA (default)
(2) DSA and Elgamal
(3) DSA (sign only)
(4) RSA (sign only)
Your selection?
RSA keys may be between 1024 and 4096 bits long.
What keysize do you want? (2048)
Requested keysize is 2048 bits
Please specify how long the key should be valid.
0 = key does not expire
= key expires in n days
w = key expires in n weeks
m = key expires in n months
y = key expires in n years
Key is valid for? (0)
Key does not expire at all
Is this correct? (y/N) y
GnuPG needs to construct a user ID to identify your key.
Real name: Hitesh
Email address: [email protected]
Comment: Welcome
You selected this USER-ID:
"Hitesh (Welcome) <[email protected]>"
Change (N)ame, (C)omment, (E)mail or (O)kay/(Q)uit? O
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
gpg: /root/.gnupg/trustdb.gpg: trustdb created
gpg: key 1A0448FECA43E1F9 marked as ultimately trusted
gpg: directory '/root/.gnupg/openpgp-revocs.d' created
gpg: revocation certificate stored as '/root/.gnupg/openpgp-revocs.d/40733A5076D11E86EF2FE5B51A0448FECA43E1F9.rev'
public and secret key created and signed.
pub rsa2048 2021-03-12 [SC]
40733A5076D11E86EF2FE5B51A0448FECA43E1F9
uid Hitesh (Welcome) <[email protected]>
sub rsa2048 2021-03-12 [E]
Note: Remember the secret key generated above.
Next, export the secret key to serverkey_private.asc and serverkey.asc file with the following command:
gpg --armor --export-secret-keys [email protected] > /var/www/passbolt/config/gpg/serverkey_private.asc
gpg --armor --export [email protected] > /var/www/passbolt/config/gpg/serverkey.asc
Next, set proper ownership to the passbolt directory:
chown -R nginx:nginx /var/www/passbolt
Next, initialize the Nginx keyring with the following command:
sudo su -s /bin/bash -c "gpg --list-keys" nginx
Output:
gpg: directory '/var/lib/nginx/.gnupg' created gpg: keybox '/var/lib/nginx/.gnupg/pubring.kbx' created gpg: /var/lib/nginx/.gnupg/trustdb.gpg: trustdb created
Next, rename the Passbolt default configuration file:
cp config/passbolt.default.php config/passbolt.php
Next, edit the passbolt.php file and define your database settings and base URL:
nano config/passbolt.php
Change the following lines:
'fullBaseUrl' => 'https://passbolt.linuxbuz.com',
// Database configuration.
'Datasources' => [
'default' => [
'host' => 'localhost',
//'port' => 'non_standard_port_number',
'username' => 'passbolt',
'password' => 'password',
'database' => 'passbolt',
'serverKey' => [
// Server private key fingerprint.
'fingerprint' => '40733A5076D11E86EF2FE5B51A0448FECA43E1F9',
'public' => CONFIG . 'gpg' . DS . 'serverkey.asc',
'private' => CONFIG . 'gpg' . DS . 'serverkey_private.asc',
Save and close the file then install the Passbolt with the following command:
cd /var/www/passbolt
sudo su -s /bin/bash -c "./bin/cake passbolt install --no-admin" nginx
You should get the following output:
All Done. Took 0.9595s Import the server private key in the keyring --------------------------------------------------------------- Importing /var/www/passbolt/config/gpg/serverkey_private.asc Keyring init OK Passbolt installation success! Enjoy! ?
Configure Nginx for Passbolt
Next, you will need to create an Nginx configuration file for Passbolt. You can create it with the following command:
nano /etc/nginx/conf.d/passbolt.conf
Add the following lines:
server {
listen 80;
server_name passbolt.linuxbuz.com;
root /var/www/passbolt;
location / {
try_files $uri $uri/ /index.php?$args;
index index.php;
}
location ~ \.php$ {
fastcgi_index index.php;
fastcgi_pass unix:/var/run/php-fpm/www.sock;
fastcgi_split_path_info ^(.+\.php)(.+)$;
include fastcgi_params;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
fastcgi_param SERVER_NAME $http_host;
}
location ~* \.(jpe?g|woff|woff2|ttf|gif|png|bmp|ico|css|js|json|pdf|zip|htm|html|docx?|xlsx?|pptx?|txt|wav|swf|svg|avi|mp\d)$ {
access_log off;
log_not_found off;
try_files $uri /webroot/$uri /index.php?$args;
}
}
Save and close the file then verify the Nginx for any syntax error:
nginx -t
Output:
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok nginx: configuration file /etc/nginx/nginx.conf test is successful
Next, restart the Nginx to apply the changes:
systemctl restart nginx
Secure Passbolt with Let's Encrypt SSL
Next, you will need to install the Certbot client to install the Let's Encrypt SSL for Passbolt. You can install it with the following command:
dnf install letsencrypt python3-certbot-nginx
Next, obtain and install an SSL certificate for your lets domain with the following command:
certbot --nginx -d passbolt.linuxbuz.com
You will be asked to provide your email address and accept the term of service:
Saving debug log to /var/log/letsencrypt/letsencrypt.log Plugins selected: Authenticator nginx, Installer nginx Enter email address (used for urgent renewal and security notices) (Enter 'c' to cancel): [email protected] - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Please read the Terms of Service at https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must agree in order to register with the ACME server. Do you agree? - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (Y)es/(N)o: Y - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Would you be willing, once your first certificate is successfully issued, to share your email address with the Electronic Frontier Foundation, a founding partner of the Let's Encrypt project and the non-profit organization that develops Certbot? We'd like to send you email about our work encrypting the web, EFF news, campaigns, and ways to support digital freedom. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (Y)es/(N)o: Y Account registered. Requesting a certificate for passbolt.linuxbuz.com Performing the following challenges: http-01 challenge for passbolt.linuxbuz.com Waiting for verification... Cleaning up challenges Deploying Certificate to VirtualHost /etc/nginx/conf.d/passbolt.conf Redirecting all traffic on port 80 to ssl in /etc/nginx/conf.d/passbolt.conf - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Congratulations! You have successfully enabled https://passbolt.linuxbuz.com - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Subscribe to the EFF mailing list (email: [email protected]). IMPORTANT NOTES: - Congratulations! Your certificate and chain have been saved at: /etc/letsencrypt/live/passbolt.linuxbuz.com/fullchain.pem Your key file has been saved at: /etc/letsencrypt/live/passbolt.linuxbuz.com/privkey.pem Your certificate will expire on 2021-06-09. To obtain a new or tweaked version of this certificate in the future, simply run certbot again with the "certonly" option. To non-interactively renew *all* of your certificates, run "certbot renew" - If you like Certbot, please consider supporting our work by: Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate Donating to EFF: https://eff.org/donate-le
Register an User for Passbolt
Next, you will need to register a user for Passbolt. You can do it with the following command:
cd /var/www/passbolt
sudo su -s /bin/bash -c "./bin/cake passbolt register_user -u [email protected] -f howtoforge -l Demo -r admin" nginx
You should get the following output:
____ __ ____
/ __ \____ _____ ____/ /_ ____ / / /_
/ /_/ / __ `/ ___/ ___/ __ \/ __ \/ / __/
/ ____/ /_/ (__ |__ ) /_/ / /_/ / / /
/_/ \__,_/____/____/_.___/\____/_/\__/
Open source password manager for teams
---------------------------------------------------------------
User saved successfully.
To start registration follow the link provided in your mailbox or here:
https://passbolt.linuxbuz.com/setup/install/f81227bc-b0b6-44b5-99a7-6b490a4ba262/5a112de0-6ca4-4e1b-97c8-26453ef3828b
You can use the above link to access the Paabolt.
Configure Firewall
Next, you will need to allow ports 80 and 443 through the firewall. You can do it with the following command:
firewall-cmd --permanent --add-port=80/tcp
firewall-cmd --permanent --add-port=443/tcp
Now, reload the firewalld to apply the changes:
firewall-cmd --reload
Access Passbolt Web UI
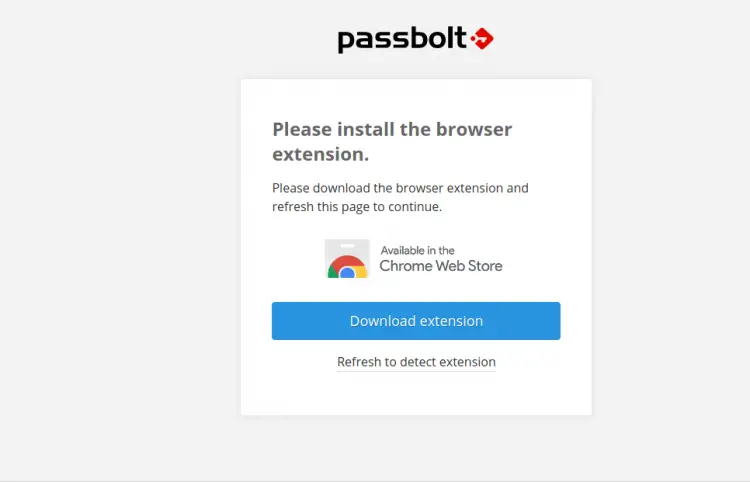
Now, open your web browser and type the URL https://passbolt.linuxbuz.com/setup/install/f81227bc-b0b6-44b5-99a7-6b490a4ba262/5a112de0-6ca4-4e1b-97c8-26453ef3828b. You will be redirected to the following page:
Here, you will need to download the Passbolt browser extensions and refresh the page once installed. You should see the following page:
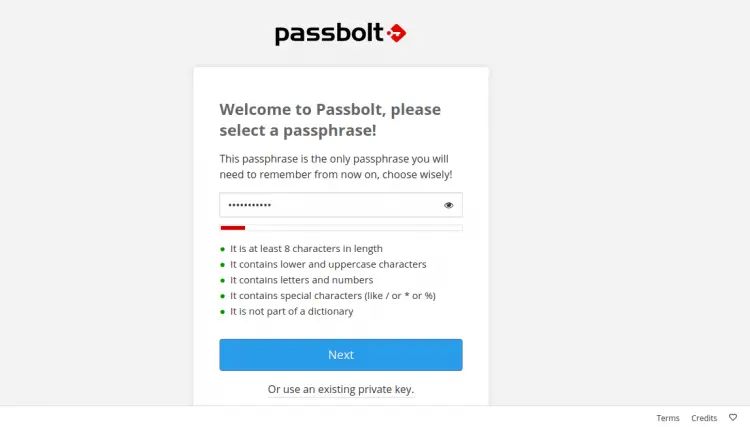
Specify the secure password and click on the Next button. You should see the following page:
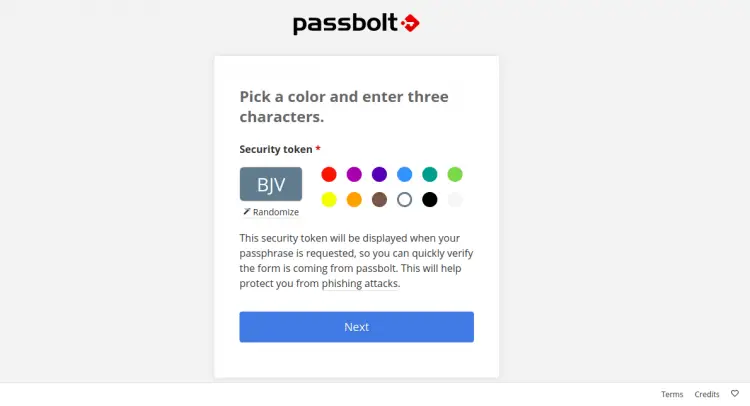
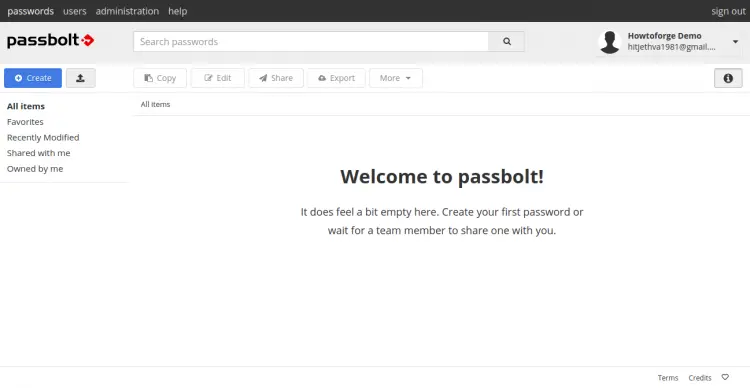
Pick a color, enter a security token and click on the Next button. You will be redirected to the Passbolt dashboard in the following page:
Conclusion
Congratulations! you have successfully installed Passbolt password manager with Nginx and Let's Encrypt SSL on CentOS 8. You can now implement the Passbolt in your organization and start storing and sharing the login credential across the team members securely.