If you’re interested in cybersecurity, then you’ve probably heard of Nmap (Network Mapper).
Nmap is a powerful free and open-source tool that can be used for a variety of tasks, from network exploration to security auditing.
In this guide, we’ll be giving a detailed tutorial on how to use Nmap. We’ll start with the basics and then move on to more advanced topics and how they can be used to identifying security issues.
By the end of this post, you should have a good understanding of how Nmap works and how it can be used to benefit your cybersecurity efforts.
Objectives
This article is aimed towards users who aren’t familiar with Nmap, and we’ll be covering the basics of Nmap with easy explanations and examples to help you along the way.
We’ll also glance at some of the advanced commands so you can get a better feel what other things Nmap can do.
The tutorial is a bit longer because it attempts to explain some basic concepts in an easy to understand manner, in hopes of giving the beginner readers a solid foundation for using Nmap confidently.
I figured that the alternative would be to give a short overview of Nmap and then you having to go through different other tutorials and videos to try to piece together different bits of information.
If there’s anything unclear, then please feel free to leave a comment and we’ll answer as soon as we can.
Table of Contents
- Objectives
- Basic Ideas
- What is Network Discovery
- Getting Started with Nmap
- Installing Nmap
- TCP/IP and Data transmission basics
- Nmap Scan Types – Host Discovery, Port Scan, OS detections, and Service detections
- Nmap commands with different options
- Basic Scans with Nmap
- Host Discovery techniques with Nmap
- Port scanning techniques with Nmap
- Service detection with Nmap
- OS detection with Nmap
- Miscellaneous Scans – Aggressive Scan
- Scan output
- Nmap Scripting Engine – NSE
- Conclusion
Basic Ideas
Before we take a deep dive into Nmap commands, we need to learn more about what it does. We already said Nmap is a network discovery tool.
In this section, we’ll be talking about what network discovery is and why is it important. If you think you’re knowledgeable enough about network discovery, you could skip this section.
What is Network Discovery
So, what is network discovery? In simple terms, network discovery is the process of finding out the devices that are on the network.
Let’s say you have your smartphone, laptop, and TV connected to the home router. So, there should be only 3 devices connected to your network.
If you are suspicious of some sketchy neighbor that might be using your Wi-Fi and want to find out how many devices are connected to your network, you could use Nmap to find it out.
This is just the tip of the iceberg – there is so much more to learn about network discovery with Nmap.
This is the first step of mapping out and monitoring a network.
System administrators use this process for keeping their network safe and secure while this is the step that determines the possibility of success for any hacker trying to gain access to the network.
Why is Network Discovery Important?
Network mapping and discovery are often used in big networks to find out their inner workings and connections.
It also plays a crucial role in cybersecurity.
We’ll use an analogy to describe how important network discovery really is.
Let’s imagine a group of robbers that’s planning a bank heist, like in the movies.
What is the first step those robbers are going to perform?
The first step most likely is information gathering.
They will try to gather information about the bank as much as they can through active or passive reconnaissance.
The will try to learn:
- How the bank operates, the building structure.
- How many gates are there, how many are open, what’s behind the door, how secure the doors are, etc.
- They will try to find a weak spot in the system. If found, this weakness will play a crucial role in their success and the plan will form around this weakness.
They will rob the bank exploiting the bank’s weakness.
Don’t get the wrong idea – the aim of this tutorial isn’t the malicious use of information gathering.
Getting back to our point, we’ll see why this network discovery is so important to keep our system secure.
Just as you might have imagined the group of robbers will be gathering information about the bank first, a malicious hacker will do the same to your network or system. They will find out:
- What devices (banks) there are in your network
- What ports are open to the internet (open doors in the bank)
- The program/service running on the open port (what’s behind the door)
- Which program has a vulnerability that the hacker can exploit (open doors with weak security)
These are some of the things that can be done through network discovery with ill intent.
Furthermore, if there is one single device on your network with security flaws, the whole network could become compromised!
How will you defend your system against such parties? By playing their game against them.
[powerkit_alert type=”info” dismissible=”false” multiline=”true”]You will also have to know your systems in and out, actively searching for potential weaknesses and removing them as soon as possible.[/powerkit_alert]
That’s why Network Discovery plays a paramount role in securing a network system and performing security audits.
Ethical hackers and penetration testers will use this technique often to find out weaknesses in the network and secure it before the hackers can take advantage of the flaw.
With all that basics out of the way, let’s get into some details of the Nmap package.
Getting Started with Nmap
Nmap is one of the most used network mappers out there. It is available for Linux, Windows, and MAC operating systems. If you are running one of the operating systems that are designed for penetration testers such as Kali Linux, Nmap should come with the OS as a pre-installed package.
However, if you are running any other operating systems, you have to install Nmap first.
Installing Nmap is pretty straightforward.
In this tutorial, we’ll cover how to install it on Linux operating system, however the Nmap commands are similar on all platforms once you install Nmap on your OS, so you should be able to go through this tutorial no matter what OS you are using.
Installing Nmap
You can find a thorough installation guide for each operating system on nmap.org. In this tutorial we’ll just go through some quick ways of installing Nmap on Ubuntu and Debian based distros, CentOS, Windows and Mac OS X.
After the installation I’ll be demonstrating using Nmap using Ubuntu, however, as mentioned before, the commands are similar on all operating systems.
Install Nmap on Ubuntu and other Debian Based Distros
To install Nmap on Ubuntu and other Debian based distros, first we’ll update the package index.
sudo apt-get update
This will update the package list from the repositories. It will not install any new packages rather it will update what packages have an upgrade available for them in the repositories.
This way you will get the most updated versions of the package you are installing.
To install Nmap, run:
sudo apt-get install nmap
When you run this command, you will be prompted to enter Y/n for confirmation. Type in Y to start the installation process. Let the system do its work and install the packages.
Install Nmap on CentOS and other RPM Based Distros
We’ll use yum in this example, but feel free to use dnf if you have it installed.
First update the package index:
sudo yum update
To install Nmap, run:
sudo yum install nmap
Install Nmap on Windows 10
The most popular way of installing Nmap on Windows is by using the self-installer.
To do this go to https://nmap.org/download.html and in the Microsoft Windows binaries section, find and download the Latest stable release self-installer, which looks like nmap-<latest version>-setup.exe, and run the installer.
At the time of writing the latest installer is nmap-7.91-setup.exe.
Install Nmap on MAC OS X
For Mac OS X you can check the installation instructions from Nmap.org to download and install the executable installer named nmap-<latest version>.dmg.
Check if Nmap is Working
After it’s done, open a command line and run the following command to check the Nmap version. This way we also know that Nmap is working.
nmap --version
Nmap version 7.91 ( https://nmap.org ) Platform: x86_64-pc-linux-gnu Compiled with: liblua-5.3.3 openssl-1.1.1d nmap-libssh2-1.8.2 libz-1.2.11 libpcre-8.39 libpcap-1.9.1 nmap-libdnet-1.12 ipv6 Compiled without: Available nsock engines: epoll poll select
You should see the version of the installed Nmap. If you do not see the version then there is something wrong with your installation.
Try to go over the steps described before once again or let us know in the comments and we’ll try to help as soon as we can.
Your installed version of Nmap could be different. No need to worry about that.
TCP/IP and Data transmission basics
Before we move on to further Nmap topics, you should know the basics of how the IP addresses and ports work together to identify the source and destination. Then how the data is transmitted between them over the internet.
IP address and the Ports
IP Adresses: The IP address is the address through which all internet communications are done. Each machine has an IP address assigned to them.
Ports: A single machine/computer might have multiple programs or applications running on it that are connected to the internet. These programs might require communicating different messages. This is accomplished with Ports.
For example, imagine a computer named “B” is connected to the internet. The computer is running two different applications named “1” and “2“.
The computer “B” will have an IP address associated with it.
The two applications “1” & “2” will also use the same IP address but they will have different Ports to distinguish them when communicating.
Data transmission basics
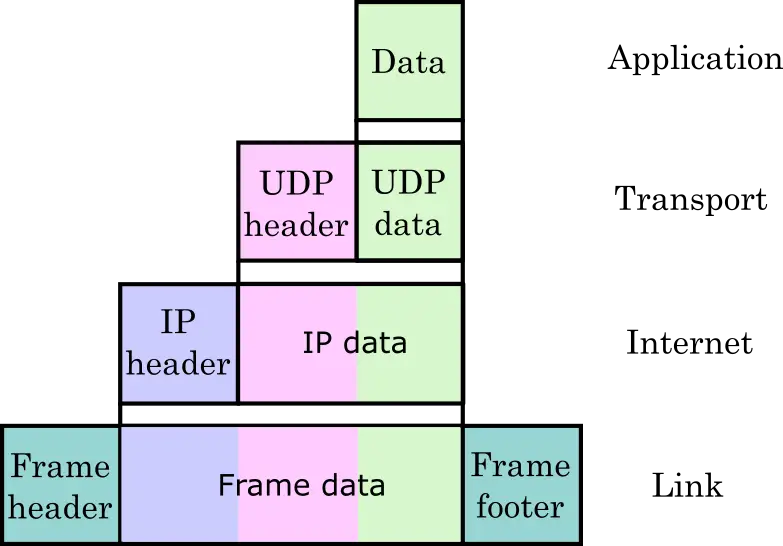
In the TCP/IP model, the 2nd layer is the transport layer and this is where communication service is provided to the running applications.
There are two transport layer protocols. The TCP (Transmission Control Protocol) and UDP (User Datagram Protocol).
- TCP: The TCP protocol is a connection-based protocol, meaning it requires establishing a connection between the source and destination before data transmission. It is reliable and implemented where data accuracy and continuity are important such as downloading files.
- UDP: Whereas, UDP is a connectionless protocol and it is used where speed is the main concern. A proper example would be online multiplayer video games.
[powerkit_alert type=”warning” dismissible=”false” multiline=”true”]Important: Having some basic ideas about these protocols is mandatory to understand how Nmap scans work.[/powerkit_alert]
Let’s see how connections are established in TCP.
The three-way handshake
TCP enables a two-way connection and makes sure the sent packets are being received in the destination endpoint. There is also a sequence of packets that needs to be maintained. TCP can only start transmitting data after establishing a connection. The connection is established through the three-way handshake.
There are 3 steps in a three-way handshake for establishing a connection:
- SYN: The client sends a “synchronize” or SYN message with a random sequence number (let’s say X).
- SYN-ACK: The server responds by a “synchronize-acknowledgement” or SYN-ACK message with its own randomly generated sequence number (let’s say Y). It also adds 1 to the client’s sequence number X, sets the number (X+1) as ACK, and sends the SYN-ACK message back to the client.
- ACK: The client “acknowledges” by sending an ACK message with the ACK set to (Y+1).
This might be a lot to take in.
To try to illustrate, please check out the image below, along with the associated explanation on the 3 step handshake.
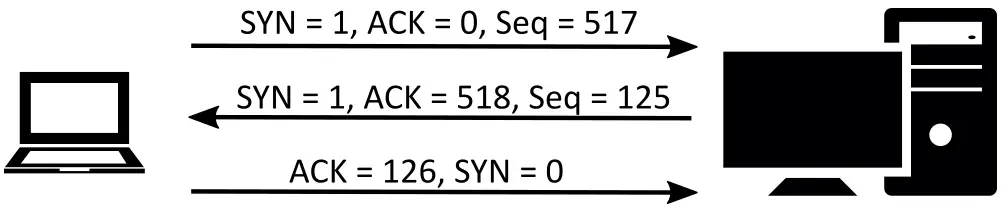
- SYN: Step 1 of a 3-way handshake – the client is sending SYN message with a random sequence number,
517(remember X, from the above explanation?). - SYN-ACK: The server generates its own random sequence number,
125(Y, from earlier) and responds to the client by sending a SYN-ACK message with the ACK set to518(X + 1 = 517 + 1 = 518). - ACK: the client responds to the server by sending an ACK message set to
126(Y + 1 = 125 + 1 = 126).
Hopefully that explanation made sense, and now you know how the TCP protocol establishes a connection between two nodes.
After the connection has been established, both the client and server can send and receive data in two-way communication.
Aside from the TCP flags SYN and ACK, some other significant flags will come up later:
- FIN: Used for terminating a connection (Finish)
- RST: Resets a connection when an unexpected packet arrives
- URG, PSH: The data packets should be processed instantly
Remember Nmap? Don’t forget we learned all this to know how Nmap scans work. Let’s move on to Nmap now.
Nmap Scan Types – Host Discovery, Port Scan, OS detections, and Service detections
Generally, Nmap scans can be divided into two types:
- Host discovery: In host discovery, we find out which devices are up on the network, more specifically, the IP addresses of the devices. We do this by scanning a range of IP addresses with Nmap.
- Port scan: In port scan, we target one or multiple IP addresses on the network and find out what ports are open i.e., which ports have running applications that are accepting connections.
Then we move on to find out further details about the running services and the applications along with the operating system and many other info. These are known as:
- Service detection
- OS detection
In the next sections, we’ll be learning how to perform all of these scans with Nmap.
Nmap commands with different options
Finally, this is what you’ve been waiting for. Let’s learn the Nmap command structures and options.
We’ll explain each of the commands in detail.
A brief word of caution before we get started
[powerkit_alert type=”warning” dismissible=”false” multiline=”true”]
Scanning networks without permission may very well be illegal, so please proceed with caution.
We are doing this for learning purposes only, and we’ll be using our private network and scanme.nmap.org for testing out some scans. You are allowed to use this address for testing some of the Nmap commands. Also, please be careful to not overload the system.
Additionally, you can always scan your personal Wi-Fi networks.[/powerkit_alert]
Nmap Command Structure
Running a simple Nmap help command will show you the basic structures and all the options for the command:
nmap -h
Nmap commands have a basic structure as follows:
nmap [ <Scan Type> ...] [ <Options> ] { <target specification> }
Scan Type and Options: We’ll explain the different options for these as we go along and perform Nmap scans.
target specification: simply means specifying our targets with their hostname, IP addresses, etc. This value can also take multiple hostnames, a range of IP addresses, and many more.
Basic Scans with Nmap
Now that you know the structure of the Nmap commands, let’s familiarize ourselves with the structures of some of the basic commands we can perform on Nmap.
Find out your private IP when you’re connected with your home router. Use the ifconfig command to see your IP on Linux.
ifconfig
Look for the inet IP address. Most private networks start with 192.168.-.-. We can see my computer’s IP address on my WiFi network in the highlighted line:
[powerkit_alert type=”info” dismissible=”false” multiline=”true”]You’re seeing private IP addresses for each interface (eth1, eth2, lo, wifi0) because each interface has its own IP address. In our case, we’re looking for my private wireless IP address.[/powerkit_alert]
eth1 Link encap:Ethernet HWaddr 00:50:56:c0:00:01 inet addr:192.168.56.1 Bcast:192.168.56.255 Mask:255.255.255.0 UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 RX packets:0 errors:0 dropped:0 overruns:0 frame:0 TX packets:0 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 RX bytes:0 (0.0 B) TX bytes:0 (0.0 B) eth2 Link encap:Ethernet HWaddr 00:50:56:c0:00:08 inet addr:192.168.74.1 Bcast:192.168.74.255 Mask:255.255.255.0 UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 RX packets:0 errors:0 dropped:0 overruns:0 frame:0 TX packets:0 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 RX bytes:0 (0.0 B) TX bytes:0 (0.0 B) lo Link encap:Local Loopback inet addr:127.0.0.1 Mask:255.0.0.0 inet6 addr: ::1/128 Scope:Global UP LOOPBACK RUNNING MULTICAST MTU:1500 Metric:1 RX packets:0 errors:0 dropped:0 overruns:0 frame:0 TX packets:0 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 RX bytes:0 (0.0 B) TX bytes:0 (0.0 B) wifi0 Link encap:UNSPEC HWaddr 10-02-B5-99-C2-A3-00-00-00-00-00-00-00-00-00-00 inet addr:192.168.43.111 Bcast:192.168.43.255 Mask:255.255.255.0 UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 RX packets:0 errors:0 dropped:0 overruns:0 frame:0 TX packets:0 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
My wireless private IP address is 192.168.43.111 and we are using a Class C subnet mask (netmask) of 255.255.255.0.
So, the IP can vary from 0-255 in my network. In other words, the devices on my network will have IP addresses ranging from 192.168.43.0 to 192.168.43.255. All of these IP addresses can be written as 192.168.43.0/24.
cmd and running ipconfig. Look for a line that reads IPv4 Address. The number across from that text is your private IP address.Let’s find out what devices are connected to my Wi-Fi router.
Finding out active hosts within a range of IP addresses
We’ll search my entire network with the following command:
nmap -sn 192.168.43.0-255
Don’t worry about the -sn part. It just tells Nmap to only find out if the device is reachable or not. We’ll learn more about this later. This command can also be written as:
nmap -sn 192.168.43.0/24
Both of these commands will look for active devices in my whole network.
Let’s take a look at the output after running one of the commands:
Starting Nmap 7.91 (https://nmap.org) at 2021-05-09 15:49 EEST Nmap scan report for 192.168.43.1 Host is up (0.012s latency). MAC Address: 80:35:C1:2C:7C:30 (Xiaomi Communications) Nmap scan report for 192.168.43.181 Host is up (0.37s latency). MAC Address: EC:D0:9E:00:B2:80 (Xiaomi Communications) Nmap scan report for 192.168.43.254 Host is up (0.18s latency). MAC Address: 12:94:BE:B5:43:73 (Unknown) Nmap scan report for 192.168.43.111 Host is up. Nmap done: 256 IP addresses (4 hosts up) scanned in 7.08 seconds
As you can see, there are four devices on my network that are up.
- The first one is the Xiaomi Router or the access point (192.168.43.1).
- The second one is also a Xiaomi Device (192.168.43.181).
- The third one is unknown probably because Nmap couldn’t figure out the vendor information.
- The last is the device itself on which we ran Nmap.
We can also see that Nmap scanned 256 IP addresses in just 7 seconds and found 4 hosts to be up.
Scanning a range of IPs
Instead of searching the whole network, we can also search some portion of the network.
nmap -sn 192.168.43.110-120
Be sure to also check the Specifying Target Hosts and Networks page, under the Practical Examples section, for a few more examples on how to specify hosts or networks to scan (it’s short and to the point).
Scanning a host with Nmap
Now that we already know which IP addresses are in my network, we can scan the hosts in detail.
Let’s scan the first device that showed up earlier, which is has the IP of 192.168.43.1:
nmap 192.168.43.1
Notice that this time we did not use the -sn flag. This will tell the Nmap to run an in-depth port scan with host discovery as well. When you scan a host like this, Nmap will scan 1000 ports in default and report back which ports are open or filtered.
Let’s see the results.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-09 16:01 EEST Nmap scan report for 192.168.43.1 Host is up (0.0056s latency). Not shown: 999 closed ports PORT STATE SERVICE 53/tcp open domain MAC Address: 80:35:C1:2C:7C:30 (Xiaomi Communications)
In the output above, you can see that Port 53 is open, and the domain service is running on the port. Nmap also states that 999 ports are closed and they are not shown.
Let’s run this command on a public network. We’ll use scanme.nmap.org, which is provided by the nice people at Nmap for testing purposes.
This time we’ll run:
nmap scanme.nmap.org
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-09 16:05 EEST Nmap scan report for scanme.nmap.org (45.33.32.156) Host is up (0.28 latency). PORT STATE SERVICE 22/tcp open ssh 80/tcp open http 646/tcp filtered ldp 1719/tcp filtered h323gatestat 1720/tcp filtered h323q931 2001/tcp filtered dc 5060/tcp filtered sip 5061/tcp filtered sip-tls 9929/tcp open nping-echo 31337/tcp open Elite 49152/tcp filtered unknown Nmap done: 1 IP address (1 host up) scanned in 36.00 seconds
This will scan the default 1000 ports on scanme.nmap.org website and report back the results.
The result is interesting. There are 11 open or filtered ports in total and we can analyze any of the ports in-depth. We’ll go over what open, closed, and filtered ports mean later in the tutorial, in the Port scanning basics section.
If you don’t want to go through all the 1000 ports, you can use the option -F to use the Fast scan which will only scan 100 well-known ports.
Let’s try that out:
nmap -F scanme.nmap.org
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-09 16:20 EEST Nmap scan report for scanme.nmap.org (45.33.32.156) Host is up (0.28 latency). PORT STATE SERVICE 22/tcp open ssh 80/tcp open http 646/tcp filtered ldp 1720/tcp filtered h323q931 2001/tcp filtered dc 5060/tcp filtered sip 49152/tcp filtered unknown Nmap done: 1 IP address (1 host up) scanned in 7.49 seconds
As you can see, it completed the scan in 7.49 seconds while the normal scan took 36 seconds.
Scanning specific ports or a range of ports
To scan a specific port we use the -p option, followed by the port:
nmap -p 22 scanme.nmap.org
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-09 16:26 EEST Nmap scan report for scanme.nmap.org (45.33.32.156) Host is up (0.31s latency). PORT STATE SERVICE 22/tcp open ssh Nmap done: 1 IP address (1 host up) scanned in 4.50 seconds
To scan a range of ports we use the -p option again, followed by the range of ports:
nmap -p 1-100 scanme.nmap.org
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-09 16:29 EEST Nmap scan report for scanme.nmap.org (45.33.32.156) Host is up (0.34s latency). Not shown: 98 closed ports PORT STATE SERVICE 22/tcp open ssh 80/tcp open http Nmap done: 1 IP address (1 host up) scanned in 5.16 seconds
For more info be sure to also check The Nmap Reference Guide – Port Specification and Scan Order. It’s short and detailed.
Scanning multiple hosts with Nmap
Now let’s look at how to run a scan on multiple hosts at the same time. We’ll use my home network again:
nmap 192.168.43.0/24
This will scan all the active devices in my network. Here’s the result:
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-09 16:35 EEST Nmap scan report for scanme.nmap.org (192.168.43.1) Host is up (0.016s latency). Not shown: 999 closed ports PORT STATE SERVICE 53/tcp open domain MAC Address: 80:35:C1:2C:7C:30 (Xiaomi Communications) Nmap scan report for 192.168.43.181 Host is up (0.022s latency). All 1000 scanned ports on 192.168.43.181 are closed MAC Address: EC:D0:9F:00:B2:80 (Xiaomi Communications) Nmap scan report for 192.168.43.254 Host is up (0.013s latency). All 1000 scanned ports on 192.168.43.254 are closed MAC Addres: 12:94:BF:B5:43:73 (Unknown) Nmap scan report for 192.168.43.111 Host is up (0.0011s latency). Not shown: 993 closed ports PORT STATE SERVICE 135/tcp open msrpc 139/tcp open netbios-ssn 445/tcp open microsoft-ds 902/tcp open iss-realsecure 912/tcp open apex-mesh 1055/tcp open ansyslmd 5054/tcp open rlm-admin Nmap done: 256 IP addresses (4 hosts up) scanned in 10.02 seconds
The output shows all the scan results for each of the devices.
Scanning 1000 ports like this on a big network might take a long time. You might have to look at an empty terminal window for a long time.
You can enable the verbose output option using the, -v flag, to see details about the run:
nmap -v 192.168.43.0/24
Now let’s mix up all the commands we learned until now:
nmap -v -p 20-23 scanme.nmap.org google.com
This command will scan port 20-23 for both scanme.nmap.org and google.com and show the details of the run on the terminal because of the -v flag.
[powerkit_alert type=”warning” dismissible=”false” multiline=”true”]We’ve used google.com to run this small scan for learning purposes. Do not scan something aggressively without permission.[/powerkit_alert]
The output of this scan shows the following:
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-09 17:59 EEST
Initiating Ping Scan at 15:10
Scanning 2 hosts [2 ports/host]
Completed Ping Scan at 15:10, 0.19s elapsed (2 total hosts)
Initiating Parallel DNS resolution of 2 hosts. at 15:10
Completed Parallel DNS resolution of 2 hosts. at 15:10, 0.01s elapsed
Initiating Connect Scan at 15:10
Scanning 2 hosts [4 ports/host]
Discovered open port 22/tcp on 45.33.32.156
Completed Connect Scan at 15:10, 2.53s elapsed (8 total ports)
Nmap scan report for scanme.nmap.org (45.33.32.156)
Host is up (0.19s latency).
Other addresses for scanme.nmap.org (not scanned): 2600:3c01::f03c:91ff:fe18:bb2f
PORT STATE SERVICE
20/tcp filtered ftp-data
21/tcp filtered ftp
22/tcp open ssh
23/tcp filtered telnet
Nmap scan report for www.google.com (172.217.20.4)
Host is up (0.041s latency).
Other addresses for www.google.com (not scanned): 2a00:1450:400d:805::2004
rDNS record for 172.217.20.4: bud02s28-in-f4.1e100.net
PORT STATE SERVICE
20/tcp filtered ftp-data
21/tcp filtered ftp
22/tcp filtered ssh
23/tcp filtered telnet
Read data files from: /usr/bin/../share/nmap
Nmap done: 2 IP addresses (2 hosts up) scanned in 2.89 seconds
Raw packets sent: 20 (832B) | Recvd: 12 (600B)
The output shows the state of 4 scanned ports for both of the hosts.
Now we’ll take a look at the techniques Nmap uses for host discovery and port scanning. This will allow us to use Nmap more efficiently.
Host Discovery techniques with Nmap
This is the first step to perform in a network discovery or mapping process.
As stated before, host discovery is finding out which devices i.e., IP addresses are connected and reachable in the network. A single host or a range of IP addresses can be scanned with Nmap to see which ones of them are up.
Nmap provides loads of options to scan flexibly according to one’s need.
For example, scanning a large range of IP addresses might be time-consuming and generate a lot of irrelevant results. Thus, system administrators sometimes prefer to scan a particular range of IPs running a specific service.
We’ll take a look at some of the common options for the host discovery in Nmap with examples.
-sL Flag (List Scan)
Using this flag will only return the list (hostname & IP addresses) for the target you specified.
This can be useful as a double check to see if you have the proper IPs for your targets.
It will only list the targets with their IP addresses and domain names, and it will not ping the hosts to see if they are up.
nmap -sL scanme.nmap.org
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-11 13:30 EEST Nmap scan report for scanme.nmap.org (45.33.32.156) Other addresses for scanme.nmap.org (not scanned): 2600:3c01::f03c:91ff:fe18:bb2f Nmap done: 1 IP address (0 hosts up) scanned in 0.50 seconds
You can also scan the IPs surrounding your target by using CIDR notation. For example we’ll run the previous command again but we’ll append /28, to enumerate the CIDR /28 network range (16 IP addresses).
nmap -sL scanme.nmap.org/28
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-11 13:37 EEST Nmap scan report for li982-144.members.linode.com (45.33.32.144) Nmap scan report for li982-145.members.linode.com (45.33.32.145) Nmap scan report for li982-146.members.linode.com (45.33.32.146) Nmap scan report for algicorp.net (45.33.32.147) Nmap scan report for li982-148.members.linode.com (45.33.32.148) Nmap scan report for li982-149.members.linode.com (45.33.32.149) Nmap scan report for li982-150.members.linode.com (45.33.32.150) Nmap scan report for li982-151.members.linode.com (45.33.32.151) Nmap scan report for li982-152.members.linode.com (45.33.32.152) Nmap scan report for li982-153.members.linode.com (45.33.32.153) Nmap scan report for li982-154.members.linode.com (45.33.32.154) Nmap scan report for li982-155.members.linode.com (45.33.32.155) Nmap scan report for scanme.nmap.org (45.33.32.156) Other addresses for scanme.nmap.org (not scanned): 2600:3c01::f03c:91ff:fe18:bb2f Nmap scan report for thirdmode.com (45.33.32.157) Nmap scan report for li982-158.members.linode.com (45.33.32.158) Nmap scan report for li982-159.members.linode.com (45.33.32.159) Nmap done: 16 IP addresses (0 hosts up) scanned in 0.57 seconds
-sn Flag (No port Scan)
This tells Nmap to avoid scanning the ports of the specified target.
This is also known as ping scan. It simply returns if the host is up or not.
This is more intrusive than the list scan, yet less intrusive than scanning the ports.
This command will issue a message consisting of an ICMP echo request, TCP SYN to port 443, and TCP ACK to port 80. This is why we needed to cover these connection terminologies.
Also, if a privileged user (root & sudo in Linux) uses this command on a local area network, ARP requests are used. This is why you need to perform your Wi-Fi scans with a privileged user to see the MAC address of the active IPs. The MAC address will give you enough details to find out the vendor of the device and help identify the device.
You have already seen this command in action before, when we introduced finding out active hosts within a range of IP addresses, and we scanned my network:
nmap -sn 192.168.43.0/24
-Pn Flag (No Ping)
Sometimes the host might try and deceive Nmap to think that it’s down when it is really up.
The ping blocks might be blocked in the host.
For these kinds of hosts, you can use -Pn flag to skip the host discovery process altogether and start further scanning to see if the host is truly down.
This is an interesting option.
Let’s look at an example.
I’ve temporarily set up a virtual machine with a static IP, from Microsoft Azure. I already know the IP address of the virtual machine. I also know that the machine is currently running.
Let’s check with Nmap if it can figure out if the host is up or not. For security reasons, I will not disclose the full IP address here:
nmap [IP address]
This command shows that the host is down. Let’s try this –
nmap -sn [IP address]
No luck with this one either. Both of the commands above fail to detect that the host is up. Let’s try with “-Pn” flag this time. We’ll also turn on the verbose flag –
nmap -v -Pn [IP address]
nmap 52.231.XX.XX
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-09 18:23 EEST Note: Host seems down. If it is really up, but blocking our ping probes. try -Pn Nmap done: 1 IP address (0 hosts up) scanned in 8.06 seconds
The output shows that the host is down.
Let’s try to run Nmap with the -sn flag, which avoids scanning ports, and just returns if the host is up or not:
nmap -sn 52.231.XX.XX
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-09 18:23 EEST Note: Host seems down. If it is really up, but blocking our ping probes. try -Pn Nmap done: 1 IP address (0 hosts up) scanned in 7.18 seconds
No luck with this one either. Both of the commands above fail to detect that the host is up. Let’s try with -Pn flag this time. We’ll also turn on the verbose flag.
nmap -v -Pn 52.231.XX.XX
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-09 18:25 EEST
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Initiating Parallel DNS resolution of 1 host. at 19:25
Completed Parallel DNS resolution of 1 host. at 19:25, 0.42s elapsed
Initiating SYN Stealth Scan at 19:25
Scanning 52.131.XX.XX [1000 ports]
Discovered open 3389/tcp on 52.231.XX.XX
Completed SYN Stealth Scan at 19:25, 24.06s elapsed (1000 total ports)
Nmap scan report for 52.231.XX.XX
Host is up (0.40s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE
3389/tcp open ms-wbt-server
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 27.98 seconds
Raw packets sent: 2010 (88.440KB) | Rcvd: 27 (1.476KB)
It looks like this time Nmap found a service using port 3389 on the IP we scanned and concluded that the host is up.
The first two scans discovered the host to be down.
But when using the -Pn flag, we can see that this flag actually turns off the host discovery first. Then scans the host assuming it was up. Look at the result of doing this – the host is discovered to be up. Not only that, Nmap has found an open port at 3389 (which is the port for Remote Desktop Protocol that my virtual machine uses).
So as we mentioned above, when describing -Pn, Nmap tried to prove that the IP is actually active trying to solicit responses from hosts or network devices using the IP.
-PS Flag (TCP SYN Ping)
Sometimes the host might block the ICMP echo requests with firewalls.
In those cases, this option can be used. A TCP SYN message is sent to the server which gets the reply of SYN-ACK from the server proving that the server is up and running.
Nmap simply responds with an RST message to the SYN-ACK message sent by the server thus never establishing a connection. An example command would be:
nmap -PS scanme.nmap.org
-PA Flag (TCP ACK Ping)
This is similar to the SYN Ping above.
This time the ACK message is sent to the server. The server replies with an RST message since the first message for establishing a connection has to be a SYN.
This proves that the server is up.
nmap -PA scanme.nmap.org
-PU Flag (UDP Ping)
The previous two scans were TCP scans.
This is the UDP scan and it will bypass the firewall rules that are designed to only filter the TCP.
nmap -PU scanme.nmap.org
Port scanning techniques with Nmap
Just like host discovery, Nmap offers a lot of options for scanning ports. This is the next step of the network discovery process.
This is the most crucial step of information gathering or reconnaissance.
We have to learn to interpret the results from Nmap scans. It is important to know all of the port states that are shown in Nmap scans and what they mean.
Port scanning basics
There are six states of the ports that are recognized by Nmap:
Open: These are the ports that are accepting packets. Finding these ports are one of the primary goals of port scanning. They are the most interesting ports and attackers will always try to exploit an open port. This is why system administrators often block them or protect them with firewalls or rules.Closed: These ports are accessible and they respond to Nmap packets. They are shown as closed since no application is listening on them. These ports are still helpful and they reveal that the host is reachable.Filtered: These are the ports that Nmap cannot determine if they are open. This is because a firewall device or some kind of packet filtering system blocks the packets from reaching the ports. This state of the port provides only a little information about the port and it is highly desirable for enhanced security.Unfiltered: This means the port is accessible by Nmap but it cannot determine whether the port is open or closed. This state will only show up as a result of the ACK scan.Open | Filtered: This state means Nmap cannot determine if the port is open or filtered. This will come up later in the tutorial.Closed | Filtered: This state means Nmap cannot determine if the port is closed or filtered.
[powerkit_alert type=”info” dismissible=”false” multiline=”true”]You can see more detailed explanations of each state in the Port scanning basics section from the Nmap Reference Guide (It’s short and to the point).[/powerkit_alert]
Let’s look at some examples:
nmap -p 20-25 scanme.nmap.org
Here, we see port 22 is open, 4 of them are closed (which means they are at least accessible), and one is filtered.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-09 18:45 EEST Nmap scan report for scanme.nmap.org (45.33.32.156) Host is up (0.19s latency). Other addresses for scanme.nmap.org (not scanned): 2600:3c01::f03c:91ff:fe18:bb2f PORT STATE SERVICE 20/tcp closed ftp-data 21/tcp closed ftp 22/tcp open ssh 23/tcp closed telnet 24/tcp closed priv-mail 25/tcp filtered smtp Nmap done: 1 IP address (1 host up) scanned in 2.93 seconds
Now let’s look at another example with Google:
nmap -p 20-25 google.com
All the ports are filtered, which provides us with little information, as we’ve said before when talking about filtered ports. From this we can determine that out of the two scans, scanme.nmap.org vs Google.com, Google is more secure in terms of ports.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-09 18:47 EEST Nmap scan report for google.com (172.217.19.110) Host is up (0.036s latency). Other addresses for google.com (not scanned): 2a00:1450:400d:808::200e rDNS record for 172.217.19.110: bud02s27-in-f14.1e100.net PORT STATE SERVICE 20/tcp filtered ftp-data 21/tcp filtered ftp 22/tcp filtered ssh 23/tcp filtered telnet 24/tcp filtered priv-mail 25/tcp filtered smtp Nmap done: 1 IP address (1 host up) scanned in 1.48 seconds
Port scanning options
Not all scans can be performed with the default SYN scan.
Different scenarios require different kinds of scans. Experts will often mix different scan techniques to get the necessary information. Knowing some of the options for scanning will give you an advantage when scanning.
Now let’s look at some of the important options available in Nmap for port scanning.
-sS (TCP SYN Scan)
This is the default and most popular scan out there. It is fast and less intrusive.
It is known as the SYN Stealth Scan since the connection is never established. It works exactly like the TCP SYN Ping. The client sends a SYN to which the server replies SYN-ACK.
But in this scan the client never responds with an ACK to complete the connection, rather sends an RST message to drop the connection.
-sT (TCP Connect Scan)
This is another option that can be used instead of SYN scan when the user does not have sufficient privileges. TCP SYN Scan is generally the better choice.
-sA (TCP ACK Scan)
In this scan, only the ACK flag will be set. This is a scan to find out if the ports are unfiltered or filtered. Unfiltered ports will respond with an RST message while the filtered ports will not respond or send certain ICMP error messages.
nmap -sA scanme.nmap.org
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-09 18:48 EEST Nmap scan report for scanme.nmap.org (45.33.32.156) Host is up (0.0033s latency). Not shown: 993 unfiltered ports PORT STATE SERVICE 646/tcp filtered ldp 1719/tcp filtered h323gatestat 1720/tcp filtered h323q931 2001/tcp filtered dc 5060/tcp filtered sip 5061/tcp filtered sip-tls 49152/tcp filtered unknown Nmap done: 1 IP address (1 host up) scanned in 0.27 seconds
It shows the filtered ports among the 1000 ports it scanned.
-sW (TCP Window Scan)
This scan tries to determine if the port is open or closed by looking at the TCP Window value of the returned RST message. This works for some systems open ports use a positive window value, while closed ports have a zero window value.
-sU (UDP Scan)
This is similar to the UDP Ping (-PU). It scans the UDP ports.
-sN / sF / sX (TCP Null, FIN, and Xmas Scan)
According to RFC 793, any packet that does not contain SYN, ACK, or RST bits will get a response with an RST when the port is closed and no response when the port is closed.
These three scans take advantage of this rule and set the other flags except SYN, ACK, and RST.
- NULL Scan (-sN) if the TCP header is
NULL - FIN Scan (-sF) when the FIN bit is set
- Xmax Scan (-sX) when the FIN, PSH, and URG bits are set, which is referred to as “lighting a packet up like the Christmas tree” (Christmas tree packet is a packet with every single option set for whatever protocol is in use)
- When no response is received the port is labeled as
open | filtered, andclosedwhen an RST is received.
The problem with this scan is it cannot determine if the port is open or filtered when it gets no response. It states the port as open | filtered.
Let’s look at an example.
We’ll use one of the filtered ports of the scanme.nmap.org that we got before with the -sA flag. Let’s use the port 646, 1719, 1720, and 2001 and perform Xmas Scan on them with -sX flag:
nmap -sX -p 646,1719,1720,2001 scanme.nmap.org
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-09 18:51 EEST Nmap scan report for scanme.nmap.org (45.33.32.156) Host is up (0.00032s latency). Other addresses for scanme.nmap.org (not scanned): 2600:3c01::f03c:91ff:fe18:bb2f PORT STATE SERVICE 646/tcp open|filtered ldp 1719/tcp open|filtered h323gatestat 1720/tcp open|filtered h323q931 2001/tcp open|filtered dc Nmap done: 1 IP address (1 host up) scanned in 1.38 seconds
As we can see, all of these ports are in open | filtered state from the Xmas Scan.
-sI (TCP Idle Scan)
This is a fascinating scan type. This scan allows you to scan without revealing your own IP address. You must provide a zombie host meeting specific criteria.
You can read more about this scan on the Nmap website, as they have a more detailed explanation (TCP Idle Scan (-sI) on Nmap).
These are some of the options you can use when running Nmap scans. There are some more advanced scans that you can take a look at on Nmap’s website, in Chaper 5. Port Sscanning Techniques and Algorithms.
Service detection with Nmap
Now that you’ve consumed so much information about Host discovery and Port scanning, it’s time to move on to more interesting stuff.
We can find out more about the services that are running on the ports with the service detection option of Nmap. Service detection is enabled by the -sV flag.
We know scanme.nmap.org has port 22 open running ssh service. We’ll try to detect the version of the ssh:
nmap -sV -p 22 scanme.nmap.org
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-09 18:53 EEST Nmap scan report for scanme.nmap.org (45.33.32.156) Host is up (0.043s latency). Other addresses for scanme.nmap.org (not scanned): 2600:3c01::f03c:91ff:fe18:bb2f PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.13 (Ubuntu Linux; protocol 2.0) Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 1.33 seconds
The output shows the version of the ssh. It is OpenSSH 6.6.1p1.
This is valuable information for anyone trying to gather information about the system.
Let’s move on to OS detection now.
OS detection with Nmap
A special feature of Nmap is that it can analyze the TCP/IP stack and crosscheck the fingerprint with its huge database of different OS. OS detection can provide useful information about the system to attack with hidden identity and many more.
Let’s run an OS detection with the flag -O on scanme.nmap.org:
nmap -O scanme.nmap.org
The output shows some of the guesses by Nmap and their possibility of being true. The most probable OS is Linux as we saw the version of the SSH installed was for Ubuntu during service detection.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-10 19:20 EEST Nmap scan report for scanme.nmap.org (45.33.32.156) Host is up (0.21s latency). Other addresses for scanme.nmap.org (not scanned): 2600:3c01::f03c:91ff:fe18:bb2f Not shown: 992 closed ports PORT STATE SERVICE 22/tcp open ssh 25/tcp filtered smtp 80/tcp open http 135/tcp filtered msrpc 139/tcp filtered netbios-ssn 445/tcp filtered microsoft-ds 9929/tcp open nping-echo 31337/tcp open Elite Aggressive OS guesses: Linux 5.0 (94%), Linux 5.4 (94%), Linux 5.0 - 5.4 (94%), HP P2000 G3 NAS device (93%), Linux 2.6.32 - 3.1 (92%), Linux 4.15 - 5.6 (92%), Linux 5.3 - 5.4 (92%), Linux 2.6.32 - 3.13 (92%), Linux 3.0 - 3.2 (92%), OpenWrt Kamikaze 7.09 (Linux 2.6.22) (92%) No exact OS matches for host (test conditions non-ideal). Network Distance: 13 hops OS detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 34.73 seconds
Let’s look at an IP on my network:
nmap -O 192.168.74.128
Here, the OS detection has successfully detected the OS to be Linux and we can also see the MAC address revealing the device to be a Virtual Machine.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-10 19:25 EEST Nmap scan report for scanme.nmap.org 192.168.74.128 Host is up (0.00010s latency). Not shown: 999 closed ports PORT STATE SERVICE 111/tcp open rpcbind MAC Address: 00:0C:29:01:BD:98 (VMware) Device type: general purpose Running: Linux 3.X|4.X OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 OS details: Linux 3.2 - 4.9 Network Distance: 1 hop OS detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 5.30 seconds
Miscellaneous Scans – Aggressive Scan
There is a popular scan used in Nmap that falls into the miscellaneous category. It is the aggressive scan that is enabled by the -A flag.
The aggressive scan is quite noisy (leaves a lot of footprints that can be traced back to the source).
It combines the OS detection (-O), Service detection (-sV), Script Scan (-sC) which performs Scan with the default scripts, and Traceroute.
Let’s see it in action:
nmap -A scanme.nmap.org
The scan has listed the open and filtered ports and it ran Service detection on the open ports with OS detection.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-10 16:18 EEST Nmap scan report for scanme.nmap.org (45.33.32.156) Host is up (0.21s latency). Other addresses for scanme.nmap.org (not scanned): 2600:3c01::f03c:91ff:fe18:bb2f Not shown: 992 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.13 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 1024 ac:00:a0:1a:82:ff:cc:55:99:dc:67:2b:34:97:6b:75 (DSA) | 2048 20:3d:2d:44:62:2a:b0:5a:9d:b5:b3:05:14:c2:a6:b2 (RSA) | 256 96:02:bb:5e:57:54:1c:4e:45:2f:56:4c:4a:24:b2:57 (ECDSA) |_ 256 33:fa:91:0f:e0:e1:7b:1f:6d:05:a2:b0:f1:54:41:56 (ED25519) 25/tcp filtered smtp 80/tcp open http Apache httpd 2.4.7 ((Ubuntu)) |_http-favicon: Nmap Project |_http-server-header: Apache/2.4.7 (Ubuntu) |_http-title: Go ahead and ScanMe! 135/tcp filtered msrpc 139/tcp filtered netbios-ssn 445/tcp filtered microsoft-ds 9929/tcp open nping-echo Nping echo 31337/tcp open tcpwrapped Aggressive OS guesses: Linux 5.0 (94%), Linux 5.4 (94%), Linux 5.0 - 5.4 (94%), HP P2000 G3 NAS device (93%), Linux 4.15 - 5.6 (93%), Linux 5.3 - 5.4 (93%), Linux 2.6.32 (92%), Infomir MAG-250 set-top box (92%), Linux 3.7 (92%), Linux 5.0 - 5.3 (92%) No exact OS matches for host (test conditions non-ideal). Network Distance: 13 hops Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel TRACEROUTE (using port 3389/tcp) HOP RTT ADDRESS 1 4.00 ms 192.168.100.1 2 6.00 ms StamAcasa.rdsnet.ro (10.0.0.1) 3 7.00 ms 10-30-2-81.rdsnet.ro (10.30.2.81) 4 21.00 ms cr01.oradea (10.220.158.179) 5 13.00 ms 10.220.186.105 6 32.00 ms bpt-b3-link.ip.twelve99.net (62.115.176.57) 7 184.00 ms ae3.cr5-sjc1.ip4.gtt.net (89.149.180.38) 8 193.00 ms ffm-bb1-link.ip.twelve99.net (62.115.137.202) 9 123.00 ms nyk-bb1-link.ip.twelve99.net (62.115.138.80) 10 126.00 ms nyk-bb2-link.ip.twelve99.net (62.115.142.222) 11 217.00 ms linode-ic342731-sjo-b21.ip.twelve99-cust.net (62.115.172.133) 12 216.00 ms 173.230.159.71 13 217.00 ms scanme.nmap.org (45.33.32.156) OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 54.49 seconds
Scan output
As seen before, Nmap scans can generate lots of information, especially when searching multiple hosts or ports together. Thus, it is important to manage the output somehow.
There are different options available for outputting the file such as – normal file output, XML output, Script Kiddie output, Grepable output, etc.
-oN (Normal Output)
This is the most commonly used output and it is easily readable too. Here’s an example:
nmap -F scanme.nmap.org -oN filename
This command will save the result of the scan to a file.
-oX (XML Output)
This command can be used by programs and scripts to automate some tasks based on a Nmap scan. An example command:
nmap -F scanme.nmap.org -oX filename
Nmap Scripting Engine – NSE
Nmap comes with many versatile scripts that can be used during scans. They are generally used with port scans for more options and flexibility.
You can automate some scans with the help of the scripts. There are many different categories of scripts that you can find details about on the Nmap website – Chapter 9. Nmap Scripting Engine.
A basic example of a scan with the default script would be:
nmap -sC 192.168.43.1
This code uses the -sC flag which tells Nmap to use the default script. You can specify different scripts by using the --script option. It is always a good idea to only run the scripts that you trust.
Conclusion
We hope this tutorial has given you a basic overview of Nmap, so you have a starting point from where to go more in-depth by yourself.
Be sure to also use the nmap -h command and the manual with man nmap command, when you run into issues, as well as the documentation at Nmap.org.
If you run into any issues and you think we can help, or have any feedback, then feel free to leave us a comment and we’ll try to help as soon as we can.



Very good job. Compliments.
Very nice, thanks for this..
Maybe a small typo in -oX example ?
Dang! Thanks so much for pointing that out!
A very detailed how-to, but why didn’t you finish it completely with explaining the the four types of NSE Scripts…? … just to get perfect 😉
Hi. Great point. You’re right.
I’ll update the tutorial (or post a separate one, depending on how this one will look after the extra NSE tutorial is added).
Thank you very much for the suggestion! I appreciate it.
Thank you for this. I’m just learning Nmap and this article is perfect for me.
Hi Ronald! Thanks so much for the kind words! I hope it’s useful to you!
Very great post! I am using these techniques much more often now.
Thank you very much for the feedback! I’m happy if it has been of any use to you!