This article is more than 1 year old
The npm registry's safe word is Socket
GitHub's JavaScript failings are someone else's opportunity
Exclusive Socket has found a way to protect developers from npm, GitHub's insufficiently safe JavaScript package manager, by wrapping it in a security blanket.
The npm registry, operated by NPM until the security biz was acquired by Microsoft's GitHub in 2020, hosts software packages for the JavaScript ecosystem. It is, by its own account, "the world's largest software registry."
In the past few years, the maliciously inclined have increasingly focused on compromising package registries like npm in what's known as a supply chain attack. Subverting a popular software library has the potential to enable widespread viral distribution.
Those running the npm registry have put in place various defenses over the years, such as npm audit, a vulnerability scanning command in the npm command line interface (CLI). But the tool's implementation leaves something to be desired and developers often ignore audit warning messages, particularly if automated resolution doesn't work.
Socket built its own vulnerability scanning system and last year made it available for free (with paid tiers for teams and organizations) for open source projects. Its scanner runs as a GitHub app on code repositories when changes are made. It catches more issues than npm audit – covering not just supply chain risk but also quality, maintenance, vulnerability, and license concerns.
Ring in some changes
But Socket's scanner is also now available as a CLI that developers can install on their machines. On Thursday, Socket updated its CLI with a safe npm command that defends developers whenever they invoke npm install or npm uninstall, which perversely can install packages amid removing others.
"npm creates what is called the 'ideal tree' for a given package.json," Feross Aboukhadijeh, told The Register. "So by removing a package you might actually change what the ideal tree is. Removing a package may remove a constraint which is keeping a package on an older version, so then npm may update those packages to a more ideal/recent version."
The reason cause for this concern is that JavaScript packages distributed via npm can be compromised. According to Aboukhadijeh, Socket has seen more than 200 packages removed just in the past 30 days.
- This JavaScript scanner hunts down malware in libraries
- Google debuts OSV-Scanner – a Go tool for finding security holes in open source
- Microsoft Azure developers targeted by 200-plus data-stealing npm packages
- Open source software has its perks, but supply chain risks can't be ignored
Aboukhadijeh said that the average npm package has 79 transitive dependencies, so installing one is likely to bring dozens of additional packages along for the ride. And vetting all of those manually is not something most people have the ability, time, or inclination to do.
While using npm audit may surface known vulnerabilities, the Socket CLI now goes deeper, thanks to the addition of the safe npm command. It can be set up by running npm install -g @socketsecurity/cli, which adds a socket command to the PATH environmental variable that specifies where executable programs can be found.
Thereafter, developers can invoke the tool by entering socket npm install instead of npm install. And aliasing the command can make this more convenient still. The org recommends adding alias npm="socket npm" to their .bashrc profile (or .zshrc, or whatever shell is being used) so that the familiar npm install invocation passes transparently to the Socket CLI.
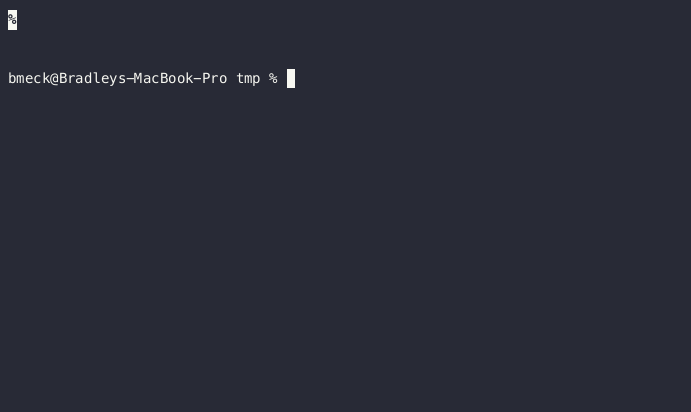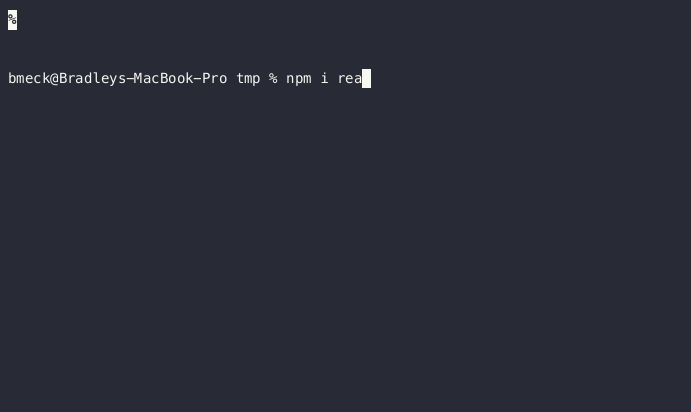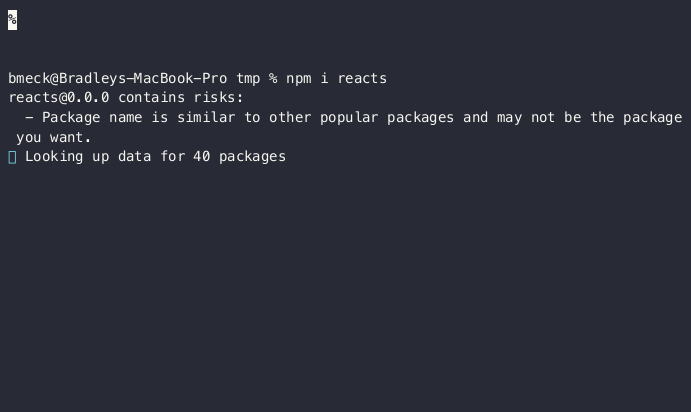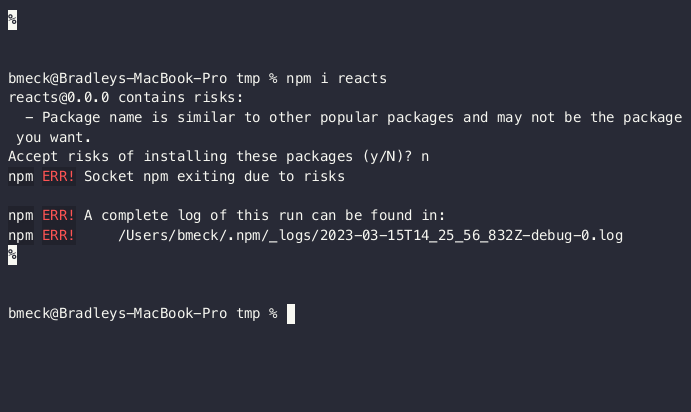
Demo of an npm command-line interaction with Socket's safety on
"Socket’s safe npm tool transparently wraps the npm command and protects the developer from malware, typosquats, install scripts, telemetry, protestware, and more – 11 issues in all," it said.
This approach can also guard against more fraught commands like npx and npm exec, which immediately execute downloaded code.
"Due to the prolific usage of these commands, we made sure to add protection for these commands too, so that you don't accidentally run bad code by copy-pasting an npx command from a README file or StackOverflow answer and get compromised," the biz promised. ®
