Linux is a popular operating system for servers and other devices. It is known for its stability, security, and flexibility. However, no operating system is immune to attack. One of the most common types of attacks against Linux servers is a brute-force attack. In this step-by-step guide, we'll show you how to install and configure fail2ban on a Linux system and how to prevent SSH brute force attacks with Fail2ban.
Before getting into the topic, let me give a brief introduction to brute-force attack and fail2ban.
Table of Contents
What is a Brute-force Attack?
A brute force attack is a type of cyberattack that tries to guess a password or other secret information by trying all possible combinations until the correct one is found.
In a brute-force attack, an attacker tries to guess a user's password by repeatedly trying different combinations of characters. This can be a very time-consuming and computationally expensive attack, but it is often successful because many people use weak passwords.
Brute force attacks can be used to gain access to a variety of things, including:
- User accounts on websites and applications,
- Password-protected files and folders,
- Encryption keys,
- Network devices,
- Computer systems.
Fortunately, there are many security software programs that can prevent brute-force attacks. Fail2ban is one of them.
What is Fail2ban?
Fail2ban is a free and open-source intrusion prevention software tool that can help to protect Linux servers from brute-force attacks. It works by monitoring the system logs for failed login attempts. If Fail2Ban detects a large number of failed login attempts from a single IP address, it will automatically block that IP address for a specified amount of time. This prevents the attacker from continuing the attack.
Fail2ban is a very versatile tool that can be used to protect a wide variety of services, including SSH, HTTP, and FTP. It is also very easy to install and configure.
Once Fail2ban is installed, you can simply specify the services that you want to protect and the number of failed login attempts that will trigger a ban.
Fail2ban is a valuable tool for any Linux administrator who wants to improve the security of their servers. It is a simple and effective way to protect against brute-force attacks, which are one of the most common threats to Linux servers.
Fail2ban is written in Python and its source code is freely available in GitHub. It should on any Linux distribution, macOS and BSD* systems.
Fail2ban Features
Fail2ban is a security tool with several user-friendly features that help protect your system from unauthorized access and attacks:
- IP Blocking: Fail2ban can automatically block IP addresses that attempt to access your system using incorrect login credentials or unauthorized methods.
- Dynamic Rules: It dynamically detects suspicious behavior in logs and creates rules to block malicious IP addresses, making it adaptable to evolving threats.
- Jail Management: Fail2ban organizes its protective measures into "jails" for different services (like SSH or web servers), making it easy to focus on specific areas of security.
- Email Alerts: It sends email notifications when suspicious activity is detected, allowing you to stay informed about potential security threats.
- Whitelisting: You can specify trusted IP addresses that should be exempt from bans to prevent accidental blocking of trusted users or services.
- Customizable Ban Times: Fail2ban lets you set how long blocked IP addresses remain banned, helping you balance security and flexibility.
- Ban Time Increments: It can increase ban times for repeat offenders, discouraging persistent attackers by making bans more prolonged with each subsequent offense.
- Whois Reports: Fail2ban can provide additional information about banned IP addresses by including whois reports in email notifications.
- Integration with Firewalls: It works seamlessly with various firewall systems (like iptables or UFW) to enforce bans effectively.
- Automatic Unbanning: Fail2ban can automatically remove IP addresses from the banned list after the ban period expires, ensuring legitimate users regain access.
- IPv6 Support: It supports both IPv4 and IPv6 addresses, making it compatible with modern networking technologies.
- Flexible Configuration: Fail2ban allows you to customize settings to match your security requirements and tailor protection to your specific environment.
In simple terms, Fail2ban is like a digital security guard that watches your system's "doors," identifies potential threats, and takes action to keep unwanted visitors out while letting trusted ones in.
Why Consider using Fail2ban? Why not just use Public Key SSH Authentication?
Why wouldn’t you just enforce public key encryption in SSH and turn off passwords? No need to bother with fail2ban when brute-forcing a password is literally impossible because it’s turned off. One of our reader asked this question.
Enforcing SSH public key-based authentication and disabling password-based authentication in SSH is indeed an effective security measure and can significantly reduce the risk of brute force attacks. However, there are a few reasons why one might still consider using Fail2ban:
- Compatibility and Convenience: Some systems or applications may require password-based authentication for certain users or scenarios. Disabling passwords entirely may not be feasible in all cases. Fail2ban provides an additional layer of security without completely eliminating the option for password authentication.
- Human Error: System configurations can sometimes be accidentally misconfigured, leaving password-based authentication inadvertently enabled. Fail2ban acts as a safety net, protecting against potential misconfigurations or changes.
- Monitoring and Reporting: Fail2ban offers logging and reporting capabilities that can provide valuable insights into authentication attempts, even if password-based authentication is disabled. These logs can be useful for auditing and identifying potential security threats.
- Complex Environments: In complex server environments, multiple services may be running with varying authentication methods. Fail2ban can be configured to protect against brute force attacks across multiple services, providing a unified security solution.
- Adaptive Security: Fail2ban's ability to adjust ban times and adapt to evolving threats makes it a flexible security tool. It can help address not only brute force attacks but also other forms of suspicious behavior.
In summary, while disabling password-based authentication and relying solely on public key encryption is a strong security practice, Fail2ban can complement this approach by offering additional security measures and adaptability in diverse server environments. It provides a more comprehensive defense against potential threats.
Prerequisites
This is a hands on guide. To follow along, make sure you have a Debian or Debian-based systems like Ubuntu.
- How To Install Debian 12 Bookworm [A Step-by-Step Guide]
- How To Install Ubuntu 22.04 LTS Server Edition
For the purpose of this guide, I will be using Debian 12 Bookworm server edition.
1. Install Fail2ban
First, update the package index on your system by running the following command:
$ sudo apt update
Then, install fail2ban by running the following command:
$ sudo apt install fail2ban
2. Configure Fail2ban to Prevent SSH Brute Force Attacks
Once the installation is complete, navigate to the configuration directory by running the following command:
$ cd /etc/fail2ban/
In this directory, you'll find the main configuration file for fail2ban named "jail.conf". However, it is recommended to make a copy of the configuration file and use the copy instead of modifying the original file.
To do so, run:
$ sudo cp jail.conf jail.local
Open the copied configuration file with your preferred text editor. In this example, we'll use nano editor:
$ sudo nano jail.local
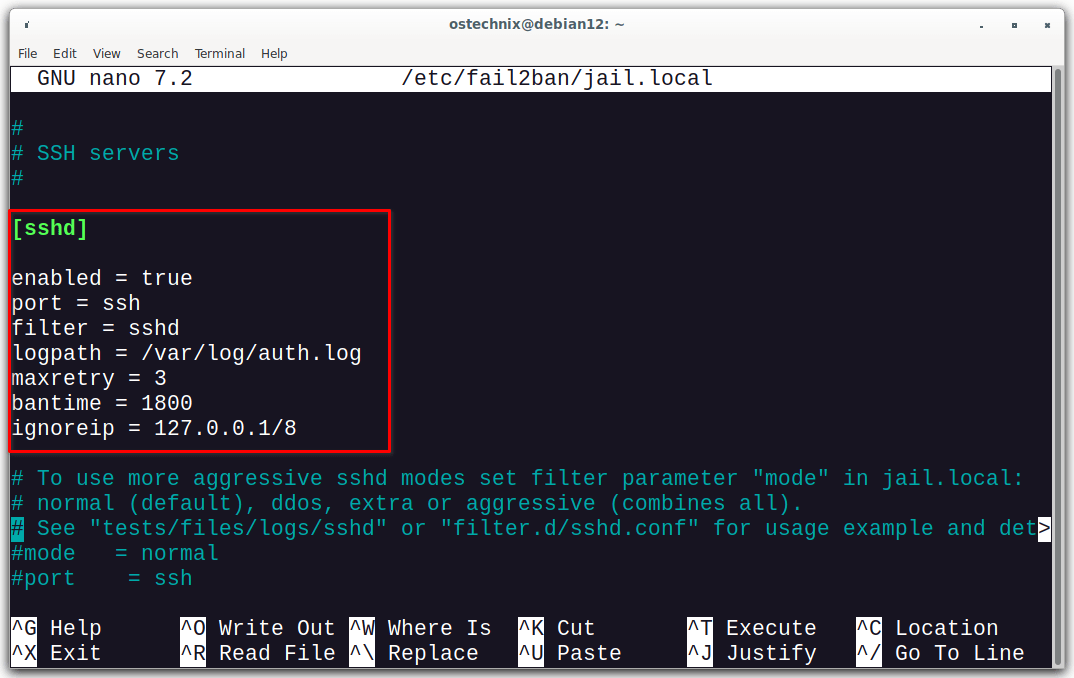
In this file, you can configure the settings for various services such as SSH, Apache, and more. For example, to configure SSH protection, locate the [sshd] section and make the following changes:
[sshd] enabled = true port = ssh filter = sshd logpath = /var/log/auth.log maxretry = 3 bantime = 1800 ignoreip = 127.0.0.1/8
This configuration sets up a Fail2ban jail named "[sshd]" to protect the SSH (Secure Shell) service. Let's break down each part:
enabled = true: This line indicates that the "sshd" jail is enabled, meaning it's active and will monitor for unauthorized access attempts.port = ssh: This specifies the port number (22 by default) where the SSH service runs. Fail2ban will monitor this port for any suspicious activity.filter = sshd: This references the name of the filter that should be applied to monitor the SSH service. The filter rules define what events to watch for and how to detect malicious behavior.logpath = /var/log/auth.log: This specifies the path to the log file (/var/log/auth.log) where authentication-related events for SSH are recorded. Fail2ban will scan this log file for signs of unauthorized access attempts.maxretry = 3: This sets the maximum number of allowed failed login attempts before Fail2ban takes action. If there are three or more consecutive failed attempts from the same IP address, Fail2ban will respond.bantime = 1800: This sets the duration in seconds for which an IP address will be banned if it exceeds the maximum number of allowed failed attempts. In this case, the ban lasts for 1800 seconds (30 minutes).ignoreip = 127.0.0.1/8: This line lists IP addresses or IP ranges that should be ignored by Fail2ban. Any attempts from these IP addresses will not be counted towards the maximum retry count. Here, localhost (127.0.0.1) is ignored. This configuration is important. It prevents you locked out of your own fail2ban server.
In summary, this Fail2ban jail configuration named "[sshd]" monitors the SSH service on the default port 22. It uses the "sshd" filter to analyze authentication events recorded in the /var/log/auth.log file. If an IP address fails to log in three or more times, it will be banned for 30 minutes. Additionally, the localhost is ignored and won't trigger bans. This configuration helps protect the SSH service from brute force attacks by temporarily banning IP addresses that show suspicious behavior.
In this example, we have shown you how to secure SSH from brute force attack. You can however configure Fail2ban to secure other services, for example FTP Apache etc., as well.
Change the above values as per your requirement. After modifying the settings, save the changes and close the file by pressing CTRL+O followed by CTRL+X keys.
Heads Up: You can also configure individual jails in the jail.d directory by creating separate .conf files for each jail. This allows you to customize settings for different services or scenarios.
3. Restart and Enable Fail2ban
Restart fail2ban to apply the new settings by running the following command:
$ sudo systemctl restart fail2ban
To ensure that fail2ban starts automatically at boot time, enable it by running the following command:
$ sudo systemctl enable fail2ban
That's it! Fail2ban is now installed and configured on your Debian system.
You can check its status by running the following command:
$ sudo systemctl status fail2ban
Sample Output:
● fail2ban.service - Fail2Ban Service
Loaded: loaded (/lib/systemd/system/fail2ban.service; enabled; preset: enabled)
Active: active (running) since Mon 2023-09-04 12:01:03 IST; 2min 54s ago
Docs: man:fail2ban(1)
Main PID: 542 (fail2ban-server)
Tasks: 5 (limit: 9347)
Memory: 19.4M
CPU: 198ms
CGroup: /system.slice/fail2ban.service
└─542 /usr/bin/python3 /usr/bin/fail2ban-server -xf start
Sep 04 12:01:03 debian12 systemd[1]: Started fail2ban.service - Fail2Ban Service.
Sep 04 12:01:03 debian12 fail2ban-server[542]: 2023-09-04 12:01:03,366 fail2ban.configreader [542]: WARNING 'allowipv6' not defined in 'Definit>
Sep 04 12:01:03 debian12 fail2ban-server[542]: Server ready4. Display Enabled Jails
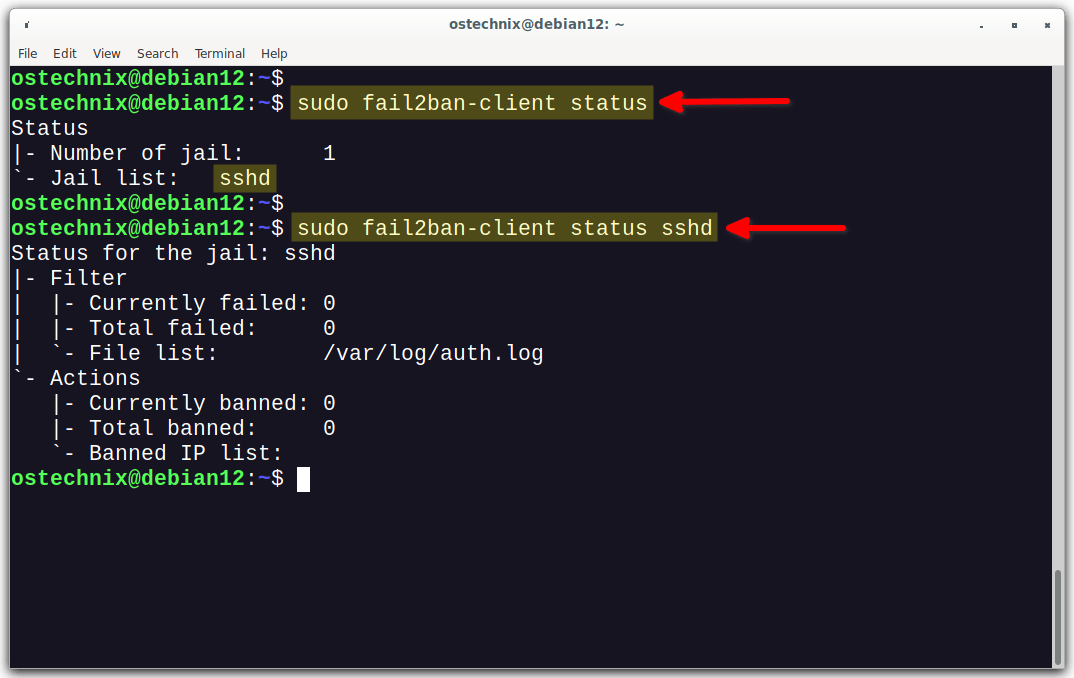
To display all enabled jails, run:
$ sudo fail2ban-client status
Sample output:
Status |- Number of jail: 1 `- Jail list: sshd
For those wondering, the fail2ban-client command is used to interact with and manage Fail2ban. It allows administrators to control and monitor the Fail2ban service and its "jails" (rules that monitor and block malicious activity).
With fail2ban-client, you can perform tasks like reloading configurations, checking status, restarting the service, banning or unbanning IP addresses and more.
If you want to display the status of a specific jail, for example sshd, run:
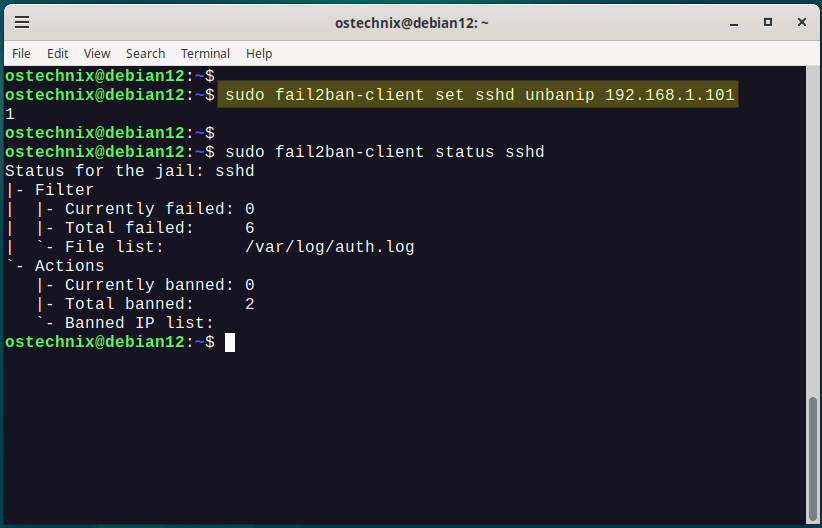
$ sudo fail2ban-client status sshd
The output shows detailed information about the status of the "sshd" jail within Fail2ban. It provides insights into the failed attempts, the log file being monitored, and any banned IP addresses.
Status for the jail: sshd |- Filter | |- Currently failed: 0 | |- Total failed: 0 | `- File list: /var/log/auth.log `- Actions |- Currently banned: 0 |- Total banned: 0 `- Banned IP list:
Here is a breakdown of what each part means in the output above.
Status for the jail: sshd: This heading indicates that the following information pertains to the "sshd" jail.Filter: This section provides information related to the filter rules that determine which events are monitored and acted upon.Currently failed: This line indicates that there are currently 0 failed attempts being tracked by the "sshd" jail.Total failed: This line indicates that there have been 0 total failed attempts recorded by the "sshd" jail.File list: /var/log/auth.log: This line specifies the log file (/var/log/auth.log) that the "sshd" jail is monitoring for authentication-related events.
Actions: This section provides information related to the actions that Fail2ban takes when malicious behavior is detected.Currently banned: This line indicates that there are currently 0 IP addresses banned by the "sshd" jail.Total banned: This line indicates that there have been 0 IP addresses banned by the "sshd" jail since it started.Banned IP list:This line shows that there are no IP addresses currently banned by the "sshd" jail.
5. Test Fail2ban
Fail2ban works by monitoring log files and detecting failed login attempts, and then banning the offending IP addresses.
Once fail2ban is installed and configured, you can test it to make sure it's working correctly. To do this, try to log in to your Fail2ban Linux server using an incorrect password several times in a row. After a few failed attempts, fail2ban should automatically block your IP address.
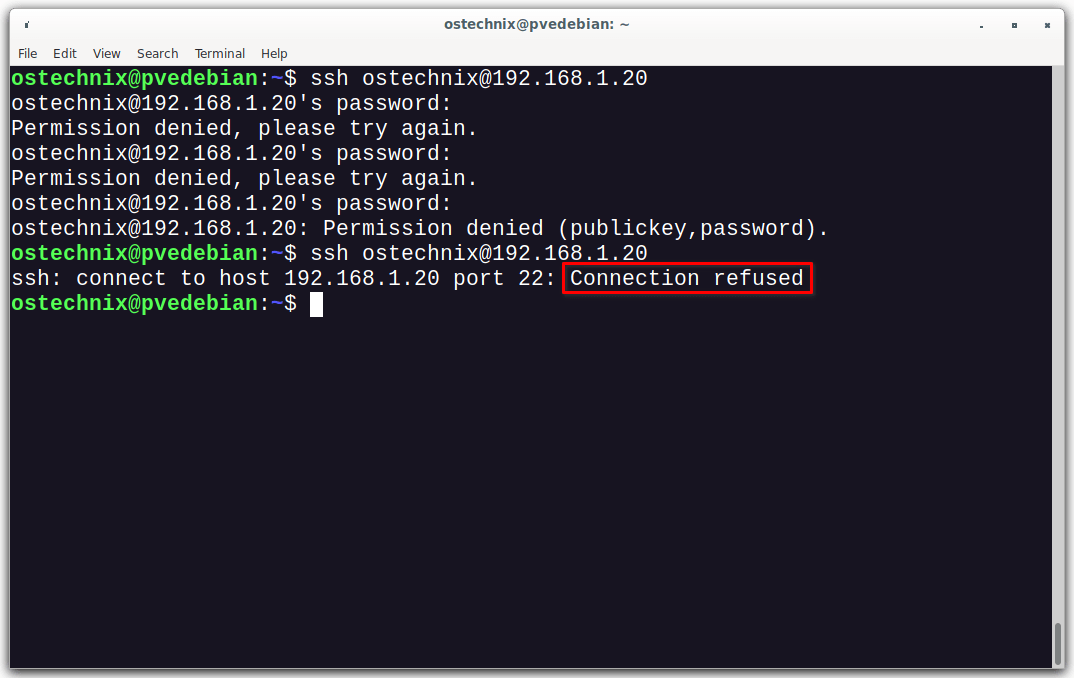
For demonstration purpose, I am going to a use Debian 11 system with an IP of 192.168.1.101 to ssh to the fail2ban server that has an IP of 192.168.1.20.
$ ssh ostechnix@192.168.1.20
After a few failed attempts, you will see the "connection refused" error.
ssh: connect to host 192.168.1.20 port 22: Connection refused
As you see in the output above, there is a connection refused error message. Meaning -fail2ban has banned the offending system.
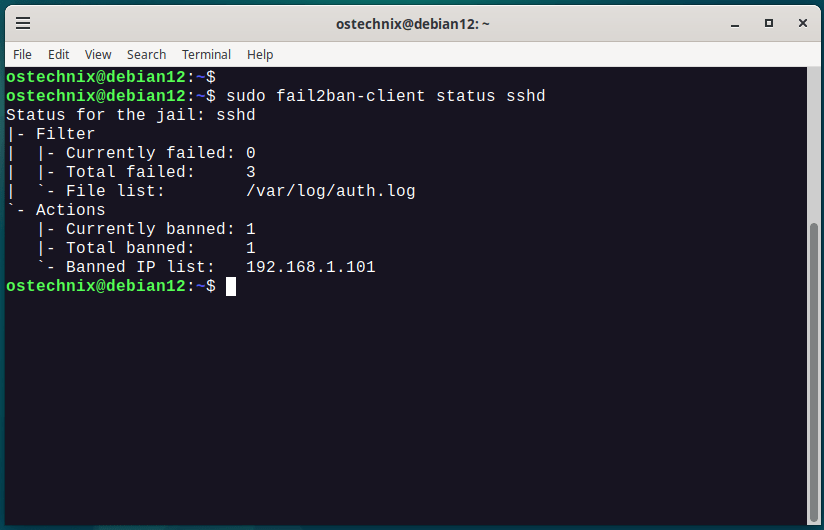
You can view the banned IP addresses by displaying the status of the sshd jail in your fail2ban server.
$ sudo fail2ban-client status sshd
Sample Output:
Status for the jail: sshd |- Filter | |- Currently failed: 0 | |- Total failed: 0 | `- File list: /var/log/auth.log `- Actions |- Currently banned: 1 |- Total banned: 1 `- Banned IP list: 192.168.1.101
As you can see, the IP address 192.168.1.101 is banned from sshd jail after repeated incorrect SSH login attempts. This IP address will be banned for 30 minutes as per my configuration. You can of course increase or decrease this time as you wish.
6. How to Manually Ban or Unban an IP Address
To manually ban or unban an IP address using Fail2ban, you can use the fail2ban-client command. Here's how you can do it:
6.1. Ban an IP Address
You can ban an IP address using the following command:
sudo fail2ban-client set <jail-name> banip <ip-address>
Replace <jail-name> with the name of the specific jail you want to apply the ban to (e.g., "sshd" for the SSH jail), and <ip-address> with the IP address you want to ban.
For example, to manually ban the IP address "192.168.1.101" in the "sshd" jail, you would use:
$ sudo fail2ban-client set sshd banip 192.168.1.101
If you want to ban a specific IP address for a custom duration within a jail, use the following command:
$ sudo fail2ban-client set <jail-name> bantime <time_in_seconds> --banip <ip_address>
Replace <jail-name> with the name of the jail, <time_in_seconds> with the desired ban duration in seconds, and <ip_address> with the IP address you want to ban.
You can check the list of banned IP addresses in a specific jail, using fail2ban-client command with "get" flag like below:
$ sudo fail2ban-client get sshd banned
For more options and usage examples, view the help section by running the following command:
$ fail2ban-client --help
Or,
$ fail2ban-client -h
6.2. Unban an IP Address
Sometimes, you might want to remove a blocked IP address from a certain jail.
To manually unban (remove the ban for) an IP address, you can use the following command:
sudo fail2ban-client set <jail-name> unbanip <ip-address>
Replace <jail-name> with the jail name (e.g., "sshd") and <ip-address> with the IP address you want to unban.
For example, to manually unban the IP address "192.168.1.101" in the "sshd" jail, you would use:
$ sudo fail2ban-client set sshd unbanip 192.168.1.101
Keep in mind that manually banning or unbanning an IP address might override the normal behavior of Fail2ban, so use these commands carefully and only when necessary.
7. Increase Ban Time for Repeat Offenders
Fail2ban provides the option to enable the "Ban Time Increment" feature, which allows you to increase the ban duration for repeat offenders automatically. This can be a powerful deterrent against persistent attackers.
Open the configuration file using your preferred text editor:
$ sudo nano /etc/fail2ban/jail.local
Inside the configuration file, find and uncomment the lines associated with the bantime.increment and bantime.factor settings.
[...] bantime.increment = true bantime.factor = 2 bantime.formula = ban.Time * (1<<(ban.Count if ban.Count<20 else 20)) * banFactor [...]
In this example, the bantime.increment setting is enabled (true), and the bantime.factor is set to 2. This means the ban time will be doubled for each subsequent ban.
After making the changes, save the configuration file and close the text editor.
To apply the changes, restart the Fail2ban service:
$ sudo systemctl restart fail2ban
With this configuration, Fail2ban will automatically increase the ban time for repeat offenders based on the specified logic. This feature can be effective in discouraging persistent attackers by making bans more prolonged with each subsequent offense. Adjust the bantime.factor setting to suit your desired level of increment.
Remember to test the configuration thoroughly to ensure it aligns with your security goals and requirements.
8. White List IP Addresses
Whitelisting an IP address involves allowing specific IP addresses to bypass Fail2ban's banning mechanisms. This is useful to prevent accidental bans for IP addresses you trust, such as your own IP address or those of trusted services.
Open the fail2ban configuration file using your preferred text editor:
$ sudo nano /etc/fail2ban/jail.local
Find the ignoreip line. Uncomment it by removing the # at the beginning of the line, if it's commented out. Then, add the IP addresses you want to whitelist, separated by spaces or commas.
ignoreip = 127.0.0.1/8 192.168.1.123 [...]
In this example, the IP address 192.168.1.123 is whitelisted. You can add more IP addresses or IP ranges following the same format.
After making the changes, save the configuration file and close the text editor.
To apply the changes, restart the Fail2ban service:
$ sudo systemctl restart fail2ban
With this configuration, the IP address you whitelisted will not be subject to Fail2ban's banning rules. It's important to whitelist only IP addresses you trust, as this could potentially undermine the security benefits of Fail2ban if done incorrectly.
9. View Fail2ban Logs
Once fail2ban is configured, you'll want to monitor it to ensure it's working correctly. You can check the fail2ban log files to see if it's detecting and blocking suspicious activity.
$ sudo tail /var/log/fail2ban.log
Sample Output:
2023-09-04 13:04:44,614 fail2ban.filter [2087]: INFO [sshd] Found 192.168.1.101 - 2023-09-04 13:04:39 2023-09-04 13:04:46,216 fail2ban.filter [2087]: INFO [sshd] Found 192.168.1.101 - 2023-09-04 13:04:46 2023-09-04 13:04:52,122 fail2ban.filter [2087]: INFO [sshd] Found 192.168.1.101 - 2023-09-04 13:04:51 2023-09-04 13:04:52,417 fail2ban.actions [2087]: NOTICE [sshd] Ban 192.168.1.101 2023-09-04 13:34:51,119 fail2ban.actions [2087]: NOTICE [sshd] Unban 192.168.1.101 2023-09-04 13:37:05,961 fail2ban.filter [2087]: INFO [sshd] Found 192.168.1.101 - 2023-09-04 13:37:05 2023-09-04 13:37:09,422 fail2ban.filter [2087]: INFO [sshd] Found 192.168.1.101 - 2023-09-04 13:37:09 2023-09-04 13:37:15,328 fail2ban.filter [2087]: INFO [sshd] Found 192.168.1.101 - 2023-09-04 13:37:14 2023-09-04 13:37:15,372 fail2ban.actions [2087]: NOTICE [sshd] Ban 192.168.1.101 2023-09-04 13:50:16,214 fail2ban.actions [2087]: NOTICE [sshd] Unban 192.168.1.101
If you want to monitor fail2ban logs in real-time, simply add -f flag.
$ sudo tail -f /var/log/fail2ban.log
You also use the grep command for locating particular details within fail2ban log files, like IP addresses, user-agents, or error messages. This enables you to narrow down your search and identify specific information you're interested in.
For instance, if you want to search and filter results containing an IP address, you would use:
$ grep "192.168.1.101" /var/log/fail2ban.log
Similarly, you can filter logs that containing a specific user-agent (E.g. Bing):
$ grep "Bing" /var/log/fail2ban.log
Filter log entries containing any Error messages.
$ grep "error" /var/log/fail2ban.log
You can also find banned or unbanned IP addresses with Date and Time as well.
To locate banned IP addresses along with their corresponding date and time, you can use the following command:
$ sudo grep 'Ban' /var/log/fail2ban.log 2023-09-04 13:04:52,417 fail2ban.actions [2087]: NOTICE [sshd] Ban 192.168.1.101 2023-09-04 13:37:15,372 fail2ban.actions [2087]: NOTICE [sshd] Ban 192.168.1.101
This will help you to track the activity of a specific IP address.
To view unbanned IP addresses with timestamp, run:
$ sudo grep 'Unban' /var/log/fail2ban.log
10. View Fail2ban Rules
By default, Fail2ban adds rules to the IPTables firewall to block IP addresses that are attempting unauthorized access. These rules are typically added to a user-defined chain specific to the jail (e.g., f2b-sshd for the SSH jail).
You can use the following command to view the rules inserted by the fail2ban:
$ sudo iptables -S
Sample Output:
-P INPUT ACCEPT -P FORWARD ACCEPT -P OUTPUT ACCEPT -N f2b-sshd -A INPUT -p tcp -m multiport --dports 22 -j f2b-sshd -A f2b-sshd -j RETURN
As you can see in the output, the lines that contain the string "f2b-" are inserted by fail2ban.
Here,
-N f2b-sshd: This line creates a new user-defined chain namedf2b-sshd. This chain will be used to manage rules related to the Fail2ban "sshd" jail, which is used to protect SSH access.-A INPUT -p tcp -m multiport --dports 22 -j f2b-sshd: This line adds a rule to theINPUTchain. It specifies that incoming TCP traffic targeting multiple ports (specified by--dports 22) should be directed to the user-defined chainf2b-sshd. This rule is used to direct traffic related to the SSH service to the Fail2ban chain.-A f2b-sshd -j RETURN: This rule is inside thef2b-sshdchain. It specifies that if a packet reaches this rule within thef2b-sshdchain, it should be returned to the previous chain (in this case, the mainINPUTchain). This rule helps optimize the processing of packets, allowing any packets that don't match the conditions set by other rules in thef2b-sshdchain to move on to other rules or chains without further processing.
To filter and view only the rules inserted by Fail2ban, you can use the -L option along with the chain name. Here's how you can do it:
sudo iptables -L <chain-name>
Replace <chain-name> with the name of the specific chain used by Fail2ban. For example, if you want to view the rules inserted by Fail2ban for the SSH jail (f2b-sshd), you would run:
$ sudo iptables -L f2b-sshd
This command will show you the rules that Fail2ban has inserted into the specified chain. It's a useful way to see which IP addresses have been banned by Fail2ban for a specific service or jail.
Keep in mind that Fail2ban's rules are managed dynamically, so the rules might change based on the detected activity and configured ban times.
You can also use grep command to filter only the rules inserted by fail2ban.
$ sudo iptables -S | grep f2b
Or,
$ sudo iptables -L | grep f2b
11. Configure Fail2ban to use UFW
As stated earlier, Fail2ban uses IPTables firewall by default to ban IP addresses. You can also change the default firewall to something else.
For instance, to configure Fail2ban to use UFW (Uncomplicated Firewall), make sure it is installed:
$ sudo apt install ufw
Open jail.local configuration file in a text editor, find the line "banaction" and set its value to ufw.
[...] banaction=ufw [...]
Save the file and close it.
Restart fail2ban service to take effect the changes.
$ sudo systemctl restart fail2ban
From now on, Fail2ban will ban the offending IP addresses using UFW.
12. Configure Email Alerts
Fail2ban is highly customizable and can be configured to monitor a wide range of log files and services. You can also customize the actions that fail2ban takes when it detects suspicious activity, such as sending an email notification or running a custom script.
Setting up email alerts in Fail2ban allows you to receive notifications about security incidents and take necessary actions. You can configure Fail2ban to send emails with whois reports to a specified email address.
To configure fail2ban for sending Email alerts, edit jail.local configuration file:
$ sudo nano /etc/fail2ban/jail.local
Inside the configuration file, find the relevant settings for email alerts. These settings are often located near the top of the file. Set the destemail to the email address where you want to receive notifications, and set the sender to the email address from which notifications will be sent.
[...] destemail = admin@example.com sender = f2b@example.com mta=sendmail [...]
In this example, admin@example.com is the email address that will receive the notifications, and f2b@example.com is the email address that will send the notifications. Replace the both mail addresses with your own.
After making the changes, save the configuration file and close the text editor.
If your system doesn't have a working email server configured, you might need to set up an email relay or configure local mail delivery. Ensure that your server is capable of sending emails.
To apply the changes, restart the Fail2ban service:
$ sudo systemctl restart fail2ban
With this configuration, Fail2ban will send email notifications to the specified email address whenever a ban is triggered. These notifications can include whois reports and other information related to the banned IP address.
13. When Not to Use Fail2ban
While Fail2ban can enhance your system's security, there are scenarios where it might not be the best solution. Here are some warnings and considerations:
- Trivial Attacks and Logging Dependence: Fail2ban is effective against basic attacks, but it relies on proper logging and the availability of a supporting daemon. If your logging is inadequate or inconsistent, Fail2ban's effectiveness could be compromised.
- Public Key Authentication Only: It is usually not necessary to use Fail2Ban with sshd if only public key authentication is enabled. If you have already configured SSH key-based authentication, fail2ban is not required.
- No Substitute for a VPN: Fail2ban is not a replacement for using a Virtual Private Network (VPN) to secure your connections. Avoid exposing services directly to the internet unless absolutely necessary.
- IP Spoofing Concerns: Fail2ban might be vulnerable to IP spoofing. If an attacker knows your IP address, he may send packets with a fake source header, potentially leading to your IP being banned. To address this, ensure you specify your fail2ban server's IP address in the
ignoreipconfiguration.
Remember, Fail2ban is a tool that complements your security measures, but it's essential to evaluate its benefits based on your specific setup and requirements.
14. How to Uninstall Fail2ban
To remove fail2ban from your Linux system, stop the fail2ban service by using the following commands:
$ sudo systemctl disable fail2ban $ sudo systemctl stop fail2ban
You can also use the following one-liner command to stop and disable the fail2ban service at once:
$ sudo systemctl disable fail2ban --now
Then uninstall fail2ban using command:
$ sudo apt remove fail2ban --purge
Frequently Asked Questions
Here's a list of commonly asked questions and their answers about Fail2ban.
A: Fail2ban is a security tool that helps protect your computer systems from unauthorized access attempts and brute force attacks by automatically banning IP addresses that show suspicious behavior.
A: Fail2ban monitors log files for specific services (like SSH or web servers). If it detects repeated failed login attempts or other malicious activity, it adds a temporary ban on the IP address responsible for the behavior.
A: A jail is a configuration setting that defines rules and actions for a specific service. It's like a container for monitoring and managing potential threats related to that service.
A: Yes, you can whitelist IP addresses you trust to prevent them from being banned accidentally. This is useful for ensuring access for known users or services.
A: Fail2ban can send email notifications when it bans an IP address. These emails might include whois reports to provide additional information about the banned IP.
A: Yes, you can specify how long an IP address remains banned after triggering the jail's rules. This allows you to balance security and flexibility.
A: Ban time increment is a feature that automatically increases the ban time for repeat offenders. With each subsequent ban, the ban duration gets longer to deter persistent attackers.
A: Yes, Fail2ban supports both IPv4 and IPv6 addresses, making it compatible with modern networking technologies.
A: Yes, Fail2ban can automatically remove IP addresses from the banned list after the ban period expires. This ensures legitimate users regain access over time.
A: Absolutely! Fail2ban's configuration is customizable to match your security requirements and tailor protection to your specific environment.
A: Yes, Fail2ban works seamlessly with various firewall systems such as iptables or UFW, enhancing your system's security measures.
A: You can configure Fail2ban to send email notifications with whois reports to a specified email address whenever suspicious activity is detected.
A: Yes, Fail2ban provides a feature to enable ban time increments, which increases the ban duration for repeat offenders. This discourages persistent attackers.
A: Yes, Fail2ban is a widely used tool to enhance server security by preventing unauthorized access attempts and protecting against brute force attacks.
A: Yes, Fail2ban offers a balance between simplicity and advanced features, making it suitable for users with varying levels of experience in system administration and security.
Conclusion
Fail2ban is an essential tool for enhancing the security of your Linux server. By monitoring log files and automatically blocking IP addresses, fail2ban can help prevent unauthorized access to your system. With the right configuration and customization, fail2ban can provide an additional layer of protection to your Linux server.
With fail2ban installed and configured on your Debian Linux server, you can protect your server from SSH brute-force attacks and other malicious activities. By following the steps in this guide, you can improve the security of your server and have peace of mind knowing that your system is protected.
Resources:
Featured image by Pete Linforth from Pixabay.


2 comments
I really like fail2ban, even though it is considered “hacky” by some. Two things I’d really like to see is:
– how to configure fail2ban for Caddy webserver (those looking for .env files are up to no good anyway)
– if its possible to get alerts through ntfy.sh instead of email.
Thanks for a great article!
We added these two topics our to-do list. We will write about these topics in the days to come. Thank you for your suggestion.