ProtonMail, the encrypted e-mail provider that buckled under crippling denial-of-service attacks even after it paid a $6,000 ransom, said it has finally recovered from the massive assaults seven days after they began.
"It has now been one week since the first attack was launched against ProtonMail," officials wrote in a blog post published Tuesday. "Since then, we have been subject to the largest and most extensive cyberattack in Switzerland, with hundreds of other companies also hit as collateral damage. In addition to hitting ProtonMail, the attackers also took down the datacenter housing our servers and attacked several upstream ISPs, causing serious damage."
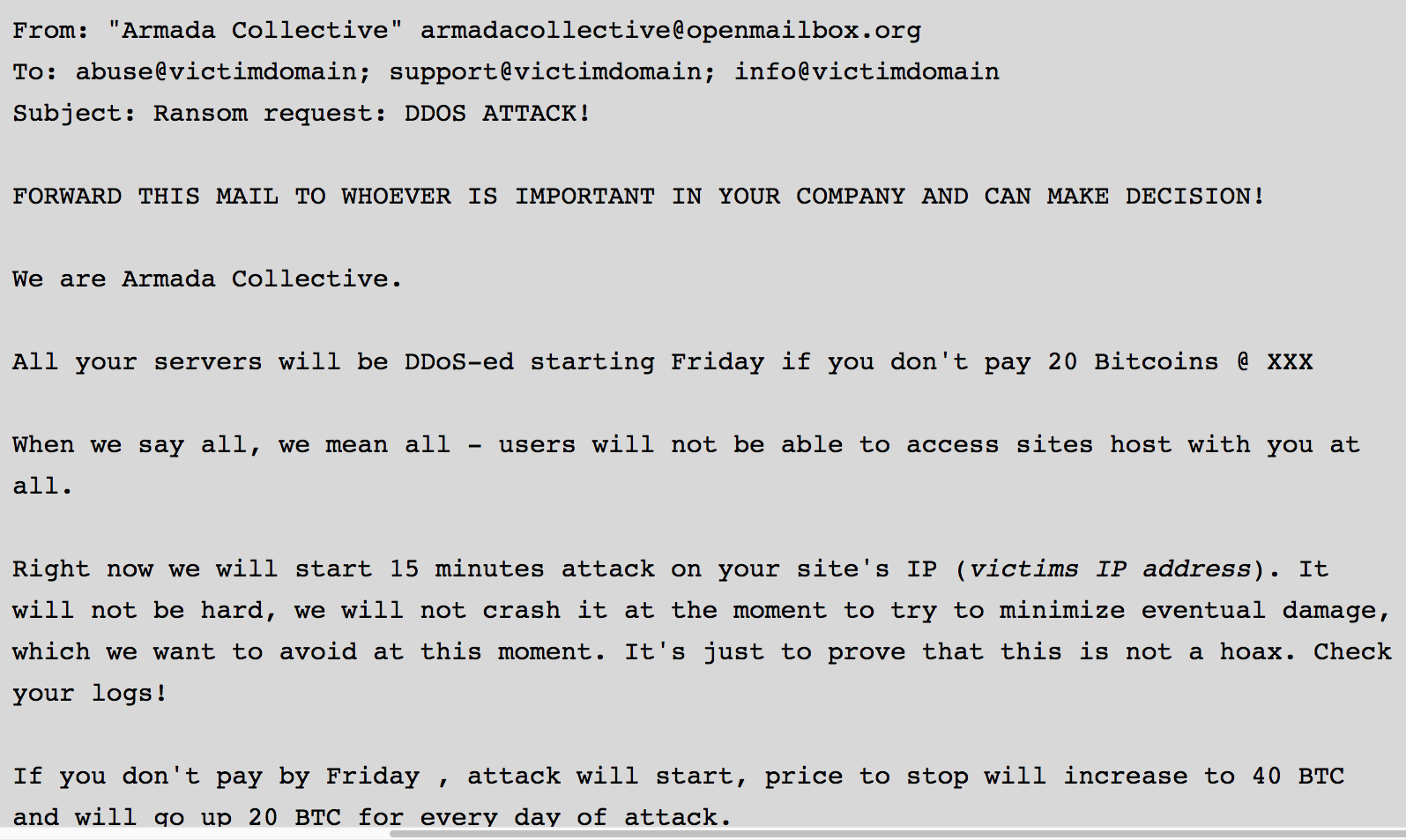
Tuesday's update still maintains that there were two waves of attacks carried out by two separate groups. The first attack, the post said, was executed by the Armada Collective, a group that performs distributed denial-of-service attacks on selected targets and then demands a ransom of thousands of dollars to get the assaults to stop. As Ars reported last week, ProtonMail was roundly criticized by many security professionals for paying the group $6,000 in bitcoins, only to come under a much more powerful attack in the following days.
The second round of attacks were much more extensive. For reasons not made public, ProtonMail officials said they were sponsored by a wealthy nation-state. Getting back online required the technical assistance of several services, including networking experts from IP-Max, service provider Level 3 Communications, and Radware, a DDoS-mitigation service. Even now, the attacks are continuing, but they're no longer capable of knocking ProtonMail offline for long periods of time. In Tuesday's post, ProtonMail officials wrote:
- ProtonMail was attacked by at least two separate groups. The first attacker, the Armada Collective, demanded a ransom, more on this can be found in the previous posts copied below. The Armada Collective has contacted us to deny responsibility for the second attack.
- The second group caused the vast majority of the damage, including the downing of the datacenter and crippling of upstream ISPs, exhibiting capabilities more commonly possessed by state-sponsored actors. They never contacted us or made any ransom demands. Their sole objective was to take ProtonMail offline, at any cost, with no regards for collateral damage, and to keep us offline for as long as possible. They have still not been identified.
- It was not until the 3rd day of attack that we realised there were two separate attackers. Given the sophistication of the attack used by the second group, we believe they may have been preparing their attack against us for some time. After seeing the first attack, they chose to strike immediately afterwards in the hopes that they would not be discovered as being a separate attacker.
- If there are DDoS experts interested in reviewing the attack data, we welcome them to contact us at security@protonmail.ch
There was no explicit mention this time that the group responsible for the second wave was sponsored by a nation-state.


 Loading comments...
Loading comments...
