Configuring Source And Destination NAT With Firewall Builder
<mike [at] netcitadel [dot] com>
http://www.fwbuilder.org
Firewall Builder is a firewall configuration and management GUI that supports configuring a wide range of firewalls from a single application. Supported firewalls include Linux iptables, BSD pf, Cisco ASA/PIX, Cisco router access lists and many more. The complete list of supported platforms along with downloadable binary packages and soure code can be found at http://www.fwbuilder.org.
In this tutorial we are going to cover how to use Firewall Builder to configure a NAT rule that translates both the source and destination IP addresses of the original packet. This type of NAT configuration can be useful in a variety of network configurations.
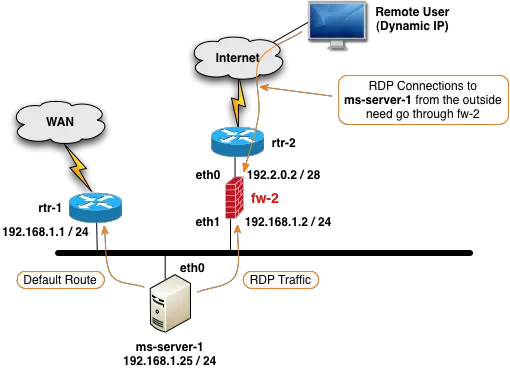
There are situations where both the source and destination IP addresses of a packet need to be NAT'ed. The diagram below shows just such a scenario where an internal server needs to be accessed remotely from the outside using the Remote Desktop Protocol (RDP).
What complicates this scenario is the fact that the default route for the ms-server-1 server directs traffic to rtr-1 instead of fw-2. If a remote user attempts to connect from the Internet to ms-server-1, and there is a destination NAT configured on the fw-2 firewall to forward traffic from a specific port on its outside eth0 interface to port 3389 (RDP) on ms-server-1, the ms-server-1 server will send the RDP response traffic to rtr-1 because of the default route and the remote desktop connection will never be established.
One way to solve this problem is to configure fw-2 with "double" NAT which results in both the original source and original destination IP addresses being modified. By modifying the source IP to be fw-2's internal eth1 address, the return packets from the ms-server-1 server for the RDP traffic will correctly be sent to fw-2 and the remote desktop connection will work.
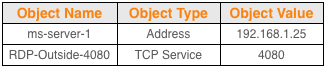
This tutorial assumes that in addition to the fw-2 firewall object the following objects and attributes have already been configured in Firewall Builder.
Firewall Builder Objects
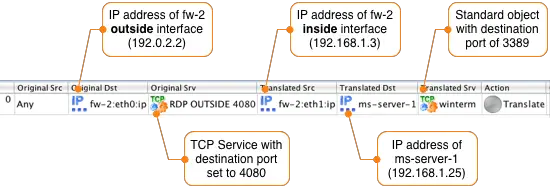
The NAT rule is created using these objects and objects from the Standard Library. After the double NAT rule is configured it should like the figure below.
NOTE: The Original Src is set to Any, this will match the IP address of any remote PC on the Internet. To connect the ms-server-1 internal server using RDP, the remote PC will connect to fw-2's outside interface on port 4080.
Here is the Firewall Builder generated compiler output for configuring this rule on an iptables firewall:
$IPTABLES -t nat -A PREROUTING -p tcp -m tcp -d 192.0.2.2 --dport 4080 -j DNAT \
--to-destination 192.168.1.25:3389
$IPTABLES -t nat -A POSTROUTING -o eth1 -p tcp -m tcp -d 192.168.1.25 \
--dport 3389 -j SNAT --to-source 192.168.1.3
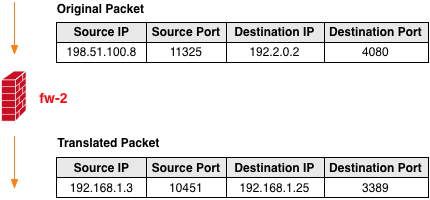
After the NAT rule is installed on the firewall the traffic that is destined to port 4080 on the outside interface of fw-2 will be translated as shown in the diagram below.
NOTE: The source ports in the example above are random and generated by the system originating the TCP connection.