How To Set Up An IPS (Intrusion Prevention System) On Fedora 17
Vuurmuur is a linux firewall manager. It takes a human readable rule syntax and turns it into the proper iptables commands. It supports logviewing, traffic shaping, connection killing and a lot of other features. Suricata is a relatively new network IDS/IPS. It's multithreaded for performance, supports IDS and IPS modes, can extract files from HTTP streams and has a lot of other features.
Fedora 17 includes both Vuurmuur and Suricata in its repository. In this howto I'll describe how to get a functional IPS using only Fedora packages.
Installing Vuurmuur and Suricata
Install both Vuurmuur and Suricata through "yum":
yum install suricata Vuurmuur-daemon Vuurmuur-tui
Running Suricata in IDS mode
As an IPS will block traffic is it is misconfigured, it's adviced to first test in the passive IDS mode.
We're getting the free Emerging Threats IDS rules optimized for Suricata and setting them up in /etc/suricata/rules/
cd /etc/suricata/
curl -O https://rules.emergingthreatspro.com/open/suricata/emerging.rules.tar.gz
tar xzvf emerging.rules.tar.gz
ln -s /etc/suricata/rules/reference.config /etc/suricata/reference.config
ln -s /etc/suricata/rules/classification.config /etc/suricata/classification.config
cp /etc/suricata/rules/suricata-1.2-prior-open.yaml /etc/suricata/suricata.yaml
Test Suricata with:
suricata -c /etc/suricata/suricata.yaml -i eth0
Leave it running for a few minutes and check /var/log/suricata/stats.log and /var/log/suricata/http.log to confirm that things work. Make sure to generate some traffic by for example opening a browser and visiting your favorite sites.
Running Suricata in IPS mode
To make sure Suricata can inspect the traffic, iptables needs to be set up to pass traffic to Suricata. We're using Vuurmuur to manage the firewall.
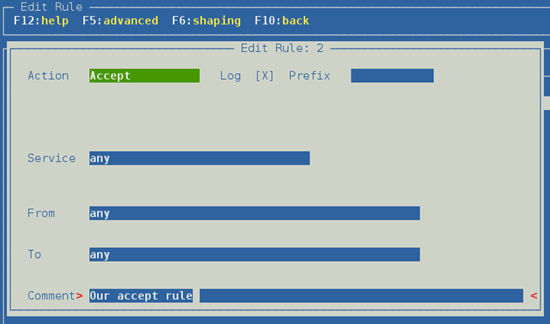
Open vuurmuur_conf, go to "Rules" and add a new rule with the following properties:
accept service any from any to any log
The rule looks like this:
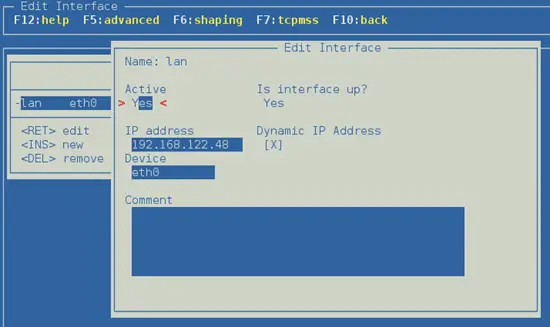
Next, to be able to start the Vuurmuur service we need to add an interface to it's configuration.
Go to "Interfaces" and add a new interface, name it however you like. In device add "eth0":
When this is done, exit vuurmuur_conf.
For Vuurmuur's logging to work properly we need to adapt the rsyslog configuration. Edit /etc/rsyslog.conf and add:
*.debug /var/log/debug
Close the file and restart rsyslog to effectuate the changes:
service rsyslog restart
We can now start Vuurmuur:
service vuurmuur start
Make sure Vuurmuur gets started on boot:
systemctl enable vuurmuur.service
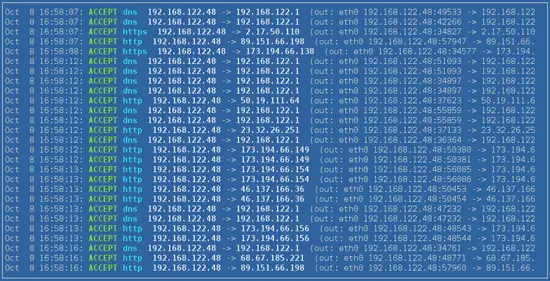
Open vuurmuur_conf, go to the logviewer and check if traffic is passing:
If thats all good, lets get to passing the traffic to Suricata for deep inspection.
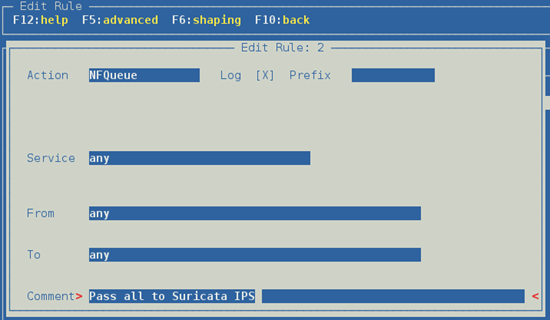
First, change the rule in vuurmuur to:
nfqueue service any from any to any
The rule looks like this:
This will pass all traffic to Suricata.
Then "apply changes" in vuurmuur_conf, this will automatically update the firewall. The logview will now show:
Then, start suricata:
suricata -c /etc/suricata/suricata.yaml -q0
Open your browser and check if traffic is flowing. Open /var/log/suricata/stats.log and /var/log/suricata/http.log to see if things are working as expected.
stats.log:
------------------------------------------------------------------- Date: 10/8/2012 -- 17:20:08 (uptime: 0d, 01h 39m 02s) ------------------------------------------------------------------- Counter | TM Name | Value ------------------------------------------------------------------- decoder.pkts | Decode1 | 3147 decoder.bytes | Decode1 | 1453192 decoder.ipv4 | Decode1 | 3147 decoder.ipv6 | Decode1 | 0 decoder.ethernet | Decode1 | 0 decoder.raw | Decode1 | 0 decoder.sll | Decode1 | 0 decoder.tcp | Decode1 | 2426 decoder.udp | Decode1 | 589 decoder.sctp | Decode1 | 0 decoder.icmpv4 | Decode1 | 0 decoder.icmpv6 | Decode1 | 0 decoder.ppp | Decode1 | 0 decoder.pppoe | Decode1 | 0 decoder.gre | Decode1 | 0 decoder.vlan | Decode1 | 0 decoder.avg_pkt_size | Decode1 | 461.770575 decoder.max_pkt_size | Decode1 | 1492 defrag.ipv4.fragments | Decode1 | 0 defrag.ipv4.reassembled | Decode1 | 0 defrag.ipv4.timeouts | Decode1 | 0 defrag.ipv6.fragments | Decode1 | 0 defrag.ipv6.reassembled | Decode1 | 0 defrag.ipv6.timeouts | Decode1 | 0 tcp.sessions | Decode1 | 76 tcp.ssn_memcap_drop | Decode1 | 0 tcp.pseudo | Decode1 | 5 tcp.invalid_checksum | Decode1 | 0 tcp.no_flow | Decode1 | 0 tcp.reused_ssn | Decode1 | 0 tcp.memuse | Decode1 | 6029312.000000 tcp.syn | Decode1 | 76 tcp.synack | Decode1 | 101 tcp.rst | Decode1 | 19 tcp.segment_memcap_drop | Decode1 | 0 tcp.stream_depth_reached | Decode1 | 0 tcp.reassembly_memuse | Decode1 | 11292544.000000 tcp.reassembly_gap | Decode1 | 0 flow_mgr.closed_pruned | FlowManagerThread | 75 flow_mgr.new_pruned | FlowManagerThread | 5 flow_mgr.est_pruned | FlowManagerThread | 101 flow.memuse | FlowManagerThread | 3690424.000000 flow.emerg_mode_entered | FlowManagerThread | 0 flow.emerg_mode_over | FlowManagerThread | 0 detect.alert | Detect | 0
http.log:
10/08/2012-17:24:02.447292 www.howtoforge.com [**] / [**] Mozilla/5.0 (X11; Linux x86_64; rv:15.0) Gecko/20100101 Firefox/15.0.1 [**] 192.168.122.48:48396 -> 188.40.16.205:80 10/08/2012-17:24:02.544458 static.howtoforge.com [**] /misc/drupal.css [**] Mozilla/5.0 (X11; Linux x86_64; rv:15.0) Gecko/20100101 Firefox/15.0.1 [**] 192.168.122.48:52942 -> 178.63.27.110:80 10/08/2012-17:24:02.549184 static.howtoforge.com [**] /modules/copyright/copyright.css [**] Mozilla/5.0 (X11; Linux x86_64; rv:15.0) Gecko/20100101 Firefox/15.0.1 [**] 192.168.122.48:52944 -> 178.63.27.110:80
Close the running suricata (ctr-c on it's console) and open /etc/sysconfig/suricata. Change "OPTIONS" to look like this:
OPTIONS="-q 0 -D --pidfile /var/run/suricata.pid"
Start Suricata through the service and make sure it's getting started at boot:
service suricata start
systemctl enable suricata.service
Dropping Traffic
So far nothing was dropped. However, we're an IPS so lets start dropping something. All the rules we downloaded default to "alert", so nothing is dropped yet.
Open /etc/suricata/suricata.yaml in your editor and scroll down to the "stream" section. There, set "inline" to "yes". This will force Suricata to do stream reassembly in a IPS aware way.
stream: memcap: 32mb checksum_validation: yes # reject wrong csums inline: yes
Add local.rules to the rules to be loaded by Suricata:
default-rule-path: /etc/suricata/rules/ rule-files: - local.rules - emerging-ftp.rules - emerging-policy.rules
Create local.rules in /etc/suricata/rules/ using a text editor. Add on a single line:
drop tcp any any -> any any (msg:"facebook is blocked"; content:"facebook.com"; http_header; nocase; classtype:policy-violation; sid:1;)
Restart Suricata:
service suricata restart
Now open Firefox, and try to go to http://www.facebook.com/, the request should time out.
The logfile /var/log/suricata/fast.log will have:
10/06/2012-11:40:49.018377 [Drop] [**] [1:1:0] facebook is blocked [**] [Classification: Potential Corporate Privacy Violation] [Priority: 1] {TCP} 192.168.122.48:57113 -> 173.252.100.16:80
10/06/2012-11:40:49.020955 [Drop] [**] [1:1:0] facebook is blocked [**] [Classification: Potential Corporate Privacy Violation] [Priority: 1] {TCP} 192.168.122.48:57114 -> 173.252.100.16:80
10/06/2012-11:40:51.991876 [Drop] [**] [1:1:0] facebook is blocked [**] [Classification: Potential Corporate Privacy Violation] [Priority: 1] {TCP} 192.168.122.48:57115 -> 173.252.100.16:80
Obviously there is a lot more to managing an IPS, but this should get you started!
Recommended further reading: