How to let users securely edit files using sudoedit on Linux
On this page
Suppose you are a system administrator in a company where teams mostly work on Linux with limited privileges. Now imagine a situation where members of one of the teams - as part of some new work - need to frequently edit a file that requires superuser privileges. What would you do?
One option is to give them the 'sudo' access, but that would be like giving a stranger access to your complete home when all they require is to be in only one of your rooms - what I mean is, default 'sudo' access will let them do anything that requires root privileges, when all that is required is the ability to edit a certain system file.
Given the kind of flexibility 'sudo' offers, the other option you have is to tweak the 'sudo' policy in a way that only the privilege to edit the file in question is granted. For example, something like this:
%newsudo ALL = vim /path/to/file
While that's no doubt a far better solution than providing the complete sudo access, there's still a loophole that someone could exploit.
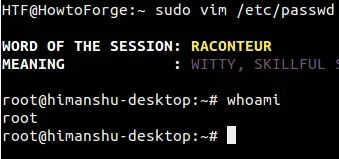
To understand what I am talking about, consider a scenario where-in the aforementioned limited access is provided to the group, and somebody opens the file in question for editing using the 'sudo' command.
Now, a clever mind with good knowledge on vim would know that they can launch a new shell from within the editor - all they have to do is to run the following vim command:
:shell
This will instantly place you in an interactive shell. If you're trying out these steps on your machine, just execute the 'whoami' command and you'll understand what loophole I was talking about - Yes, you are in the shell as root.
Here's an example screenshot:
Needless to say, the purpose of providing editing access to only a single file got defeated, and the user can do ANYTHING now.
Let's see if there's any other option we have. There exists a NOEXEC tag which you can use in your sudoers entry:
%newsudo ALL = NOEXEC: vim /path/to/file
NOEXEC basically allows you to prevent a program run by sudo from executing any other programs. So, is this the ultimate solution? Sadly no. As for the reasons, here's how the sudoers manual explains this tag:
noexec
Many systems that support shared libraries have the ability to override default library functions by pointing an environment variable (usually LD_PRELOAD) to an alternate shared library. On such systems, sudo's noexec functionality can be used to prevent a program run by sudo from executing any other programs. Note, however, that this applies only to native dynamically-linked executables. Statically-linked executables and foreign executables running under binary emulation are not affected.
The noexec feature is known to work on SunOS, Solaris, *BSD, Linux, IRIX, Tru64 UNIX, MacOS X, HP-UX 11.x and AIX 5.3 and above.
...
...
...
To enable noexec for a command, use the NOEXEC tag as documented in the User Specification section above. Here is that example again:
aaron shanty = NOEXEC: /usr/bin/more, /usr/bin/vi
This allows user aaron to run /usr/bin/more and /usr/bin/vi with noexec enabled. This will prevent those two commands from executing other commands (such as a shell). If you are unsure whether or not your system is capable of supporting noexec you can always just try it out and check whether shell escapes work when noexec is enabled.
Note that restricting shell escapes is not a panacea. Programs running as root are still capable ofmany potentially hazardous operations (such as changing or overwriting files) that could lead to unintended privilege escalation.
...
...
...
If you carefully read the text highlighted in bold, you'll know that NOEXEC has its own set of limitations.
So, what's the most reliable solution then? Well, it's sudoedit. Even sudoers manual also recommends this tool:
In the specific case of an editor, a safer approach is to give the user permission to run sudoedit.
Sudoedit
Sudoedit is a built-in command that allows users to securely edit files. According to the sudo man page, 'sudoedit' is equivalent to executing 'sudo' with the '-e' command line option.
Why is it better
With 'sudoedit', users have the choice to use their preferred editor - which is unlike the solution we discussed in the beginning of this tutorial where-in users are forced to use the Vim editor - allowing them to enjoy their own customizations. And the biggest reason of all, with 'sudoedit', user will be editing the file as themselves, and not 'root'.
How Sudoedit works
To use sudoedit, the entry in the sudoers should be, for example, something like this:
%newsudo ALL = sudoedit /path/to/file
And users that are part of the 'newsudo' group will be able to edit the file by running the following command:
sudoedit /path/to/file
So what this command will do is, it will first create a temporary copy of the file you want to edit. Then, the command will search the SUDO_EDITOR, VISUAL and EDITOR environment variables (in that order) to determine which editor should be invoked to open the temporary copy that has just been created. After the user is done with the modification work, the changes are copied back to the original file.
Here's the detailed explanation from the 'sudo' command man page:
-e, --edit
Edit one or more files instead of running a command. In lieu of a path name, the string "sudoedit" is used when consulting the security policy. If the user is authorized by the policy, the followingsteps are taken:
1. Temporary copies are made of the files to be edited with
the owner set to the invoking user.
2. The editor specified by the policy is run to edit the
temporary files. The sudoers policy uses the
SUDO_EDITOR, VISUAL and EDITOR environment variables (in
that order). If none of SUDO_EDITOR, VISUAL or EDITOR
are set, the first program listed in the editor
sudoers(5) option is used.
3. If they have been modified, the temporary files are
copied back to their original location and the temporary
versions are removed.
If the specified file does not exist, it will be created. Note that unlike most commands run by sudo, the editor is run with the invoking user's environment unmodified. If, for some reason, sudo is unable to update a file with its edited version, the user will receive a warning and the edited copy will remain in a temporary file.
Conclusion
By now, you should have a basic idea about 'sudoedit', including when to use it, and why it is better than using 'sudo' when all you want is to edit a file, or a few files. Of course, like any other security-related tool, 'sudoedit' has had its share of exploits, but it's still a recommended solution in many use cases.