Securing Your Server With A Host-based Intrusion Detection System
Version 1.0
Author: Falko Timme
This article shows how to install and run OSSEC HIDS, an Open Source Host-based Intrusion Detection System. It performs log analysis, integrity checking, rootkit detection, time-based alerting and active response. It helps you detect attacks, software misuse, policy violations and other forms of inappropriate activities.
With OSSEC HIDS you can monitor multiple systems, with one system being the OSSEC HIDS server and the others the OSSEC HIDS agents that report back to the server. However, in this tutorial I want to monitor just one system, so I perform a "local" installation so that OSSEC HIDS will do its work locally on that system.
In the following I use a Debian Sarge (3.1) system to install OSSEC HIDS on.
I want to say first that this is not the only way of setting up such a system. There are many ways of achieving this goal but this is the way I take. I do not issue any guarantee that this will work for you!
1 Installing OSSEC HIDS
Installing OSSEC HIDS is very easy, it's just a matter of downloading the sources, running the installation script and answering the questions of the installation script. First, we download and unpack the OSSEC HIDS sources:
cd /tmp
wget http://www.ossec.net/files/ossec-hids-0.9-1a.tar.gz
tar xvfz ossec-hids-0.9-1a.tar.gz
Then we run the installation script:
cd ossec-hids-0.9-1a
./install.sh
The installation script will ask you a few questions:
** Para instalação em português, escolha [br].
** Fur eine deutsche Installation wohlen Sie [de].
** For installation in English, choose [en].
** Para instalar en Español , eliga [es].
** Pour une installation en français, choisissez [fr]
** Per l'installazione in Italiano, scegli [it].
** æ¥æ¬èªã§ã¤ã³ã¹ãã¼ã«ãã¾ãï¼é¸æãã¦ä¸ãã
ï¼[jp].
** Aby instalowaÄ w jÄzyku Polskim, wybierz [pl].
** ÐÐ»Ñ Ð¸Ð½ÑÑÑÑкÑий по ÑÑÑановке на ÑÑÑÑком ,введиÑе [ru].
** Türkçe kurulum için seçin [tr].
(en/br/de/es/fr/it/jp/pl/ru/tr) [en]: <-- en (or one of the other options, if you don't want to use English)
OSSEC HIDS v0.9-1 Installation Script - http://www.ossec.net
You are about to start the installation process of the OSSEC HIDS.
You must have a C compiler pre-installed in your system.
If you have any questions or comments, please send an e-mail
to [email protected] (or [email protected]).
- System: Linux server1.example.com 2.6.8-2-386
- User: root
- Host: server1.example.com
-- Press ENTER to continue or Ctrl-C to abort. -- <-- [ENTER]
1- What kind of installation do you want (server, agent, local or help)? <-- local
- Choose where to install the OSSEC HIDS [/var/ossec]: <-- /var/ossec
3.1- Do you want e-mail notification? (y/n) [y]: <-- y
- What's your e-mail address? <-- [email protected] (please enter your own email address here)
- We found your SMTP server as: mail.example.com.
- Do you want to use it? (y/n) [y]: <-- y (normally you can accept the installer's proposal, unless you want to use another SMTP server)
3.2- Do you want to run the integrity check daemon? (y/n) [y]: <-- y
3.3- Do you want to run the rootkit detection engine? (y/n) [y]: <-- y
- Do you want to enable active response? (y/n) [y]: <-- y
- Do you want to enable the firewall-drop response? (y/n) [y]: <-- y
- Do you want to add more IPs to the white list? (y/n)? [n]: <-- n (unless you want to whitelist more IP addresses)
3.6- Setting the configuration to analyze the following logs:
-- /var/log/messages
-- /var/log/auth.log
-- /var/log/syslog
-- /var/log/mail.info
- If you want to monitor any other file, just change
the ossec.conf and add a new localfile entry.
Any questions about the configuration can be answered
by visiting us online at http://www.ossec.net .
--- Press ENTER to continue --- <-- [ENTER]
- System is Linux (SysV).
- Init script modified to start OSSEC HIDS during boot.
Adding system startup for /etc/init.d/ossec ...
/etc/rc0.d/K20ossec -> ../init.d/ossec
/etc/rc1.d/K20ossec -> ../init.d/ossec
/etc/rc6.d/K20ossec -> ../init.d/ossec
/etc/rc2.d/S20ossec -> ../init.d/ossec
/etc/rc3.d/S20ossec -> ../init.d/ossec
/etc/rc4.d/S20ossec -> ../init.d/ossec
/etc/rc5.d/S20ossec -> ../init.d/ossec
- Configuration finished properly.
- To start OSSEC HIDS:
/var/ossec/bin/ossec-control start
- To stop OSSEC HIDS:
/var/ossec/bin/ossec-control stop
- The configuration can be viewed or modified at /var/ossec/etc/ossec.conf
Thanks for using the OSSEC HIDS.
If you have any question, suggestion or if you find any bug,
contact us at [email protected] or using our public maillist at
[email protected]
(http://mailman.underlinux.com.br/mailman/listinfo/ossec-list).
More information can be found at http://www.ossec.net
--- Press ENTER to finish (maybe more information below). --- <-- [ENTER]
That's it, OSSEC HIDS is now installed and ready to be started.
2 Starting And Running OSSEC HIDS
In order to start OSSEC HIDS, we run this command:
/etc/init.d/ossec start
The output should look like this:
server1:/etc/init.d# /etc/init.d/ossec start
Starting OSSEC HIDS v0.9-1 (by Daniel B. Cid)...
Started ossec-maild...
Started ossec-execd...
Started ossec-analysisd...
Started ossec-logcollector...
Started ossec-syscheckd...
Completed.
server1:/etc/init.d#
As you might have seen during OSSEC HIDS installation, the installer also created the necessary system startup links for OSSEC HIDS, so that OSSEC HIDS will be started automatically whenever you boot/reboot your system.
After OSSEC HIDS has been started, it will run silently in the background, performing log analysis, integrity checking, rootkit detection, etc. You can check that it's running by executing
ps aux
In the output you should find something like this:
ossecm 2038 0.0 0.4 1860 792 ? S 12:40 0:00 /var/ossec/bin/ossec-maild root 2042 0.0 0.3 1736 648 ? S 12:40 0:00 /var/ossec/bin/ossec-execd ossec 2046 0.2 0.5 2192 1136 ? S 12:40 0:00 /var/ossec/bin/ossec-analysisd root 2050 0.0 0.2 1592 556 ? S 12:40 0:00 /var/ossec/bin/ossec-logcollector root 2054 12.2 0.3 1756 616 ? S 12:40 0:05 /var/ossec/bin/ossec-syscheckd
The OSSEC HIDS log file is /var/ossec/logs/ossec.log, so you can check it to see what's going on, e.g. with the tail command.
tail -f /var/ossec/logs/ossec.log
shows what's happening in real-time. Press CTRL-C to leave it.
tail -n 100 /var/ossec/logs/ossec.log
shows you the last 100 lines of the OSSEC HIDS log.
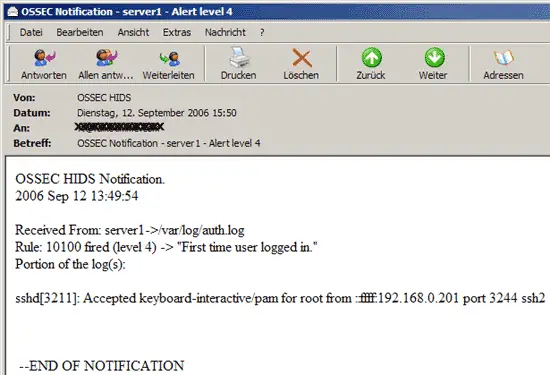
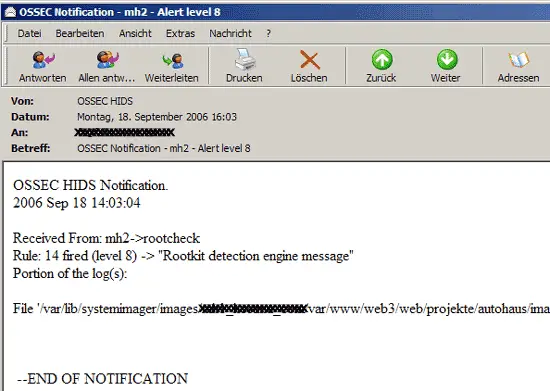
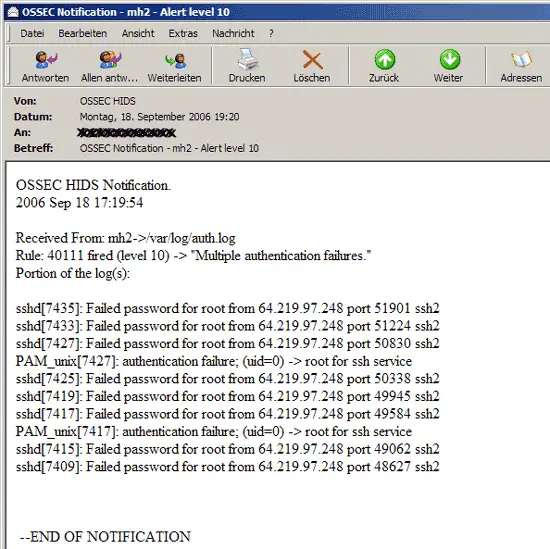
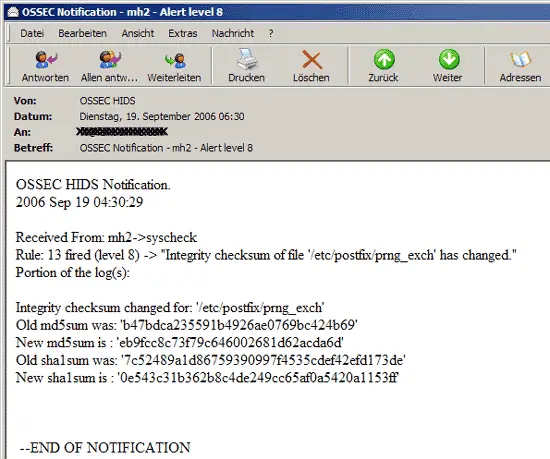
Whenever OSSEC HIDS detects something suspicious, it sends an email with a report about the activity to the email address you specified during installation:
If you want to change OSSEC HIDS' settings (e.g. change the email address, add custom rulesets, etc.), you can do this by editing the configuration file /var/ossec/etc/ossec.conf (which is in XML format). You can do this by using a command-line editor such as vi:
vi /var/ossec/etc/ossec.conf
The file looks like this:
<ossec_config>
<global>
<email_notification>yes</email_notification>
<email_to>[email protected]</email_to>
<smtp_server>mail.example.com.</smtp_server>
<email_from>[email protected]</email_from>
</global>
[...]
|
If you change the file, make sure to restart OSSEC HIDS afterwards:
/etc/init.d/ossec restart
In order to learn how to add custom rulesets, etc. to the OSSEC HIDS configuration, please refer to the OSSEC HIDS manual: http://www.ossec.net/en/manual.html
3 Links
- OSSEC HIDS: http://www.ossec.net