missinformation
|
| Author | Content |
|---|---|
| mbaehrlxer Sep 19, 2013 10:27 PM EDT |
http://xkcd.com/936/ read that, and follow it. it's all you need for a hard to crack password. greetings, eMBee. |
| djohnston Sep 20, 2013 3:38 AM EDT |
Misinformation? How did you arrive at that conclusion? Seems that the XKCD cartoon generated some buzz at the time among the cryptoanalysis crowd. In any case, both the XKCD cartoon and DarkDuck are using passphrases. XKCD's is based on dictionary words strung together, whereas DarkDuck's are the first letter of each word in the lines of a song. According to Johannes Ullrich's Theoretical and Practical Password Entropy article,Quoting:The basic dilemma is that you need to come up with a password that is hard to guess for others but easy enough for you to remember. I'd say both XKCD's and DarkDuck's examples qualify in that respect. Johannes futher states that: Quoting:Pass phrases, as suggested by the cartoon, are one solution. But once an attacker knows that you use a pass phrase, the key space is all for [sic] sudden limited again. There has been some research showing that a library of 3 word phrases pulled from wikipedia makes a decent dictionary to crack these passwords. The standard formula for calculating password entropy is 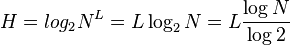 as discussed here on Shay Ben Moshe's blog entry on the XKCD cartoon. Anyway, he created a handy little javascript tool for calculating password entropy, based on the number of characters used and the total number of characters in the set. (If there are any NoScript users who want to try the javascript app on the page, the calculator is the only javascript app there. I just did "temporarily allow all on this page".) The "correct horse battery staple" phrase used in the cartoon shows an entropy of 147.99 bits, not the value of 44 bits shown in the cartoon. Some websites do not allow spaces in the password field, so all examples I use will contain no space delimiters. And the bit values were derived from Shay's javascript-based entropy calculator. as discussed here on Shay Ben Moshe's blog entry on the XKCD cartoon. Anyway, he created a handy little javascript tool for calculating password entropy, based on the number of characters used and the total number of characters in the set. (If there are any NoScript users who want to try the javascript app on the page, the calculator is the only javascript app there. I just did "temporarily allow all on this page".) The "correct horse battery staple" phrase used in the cartoon shows an entropy of 147.99 bits, not the value of 44 bits shown in the cartoon. Some websites do not allow spaces in the password field, so all examples I use will contain no space delimiters. And the bit values were derived from Shay's javascript-based entropy calculator.correcthorsebatterystaple = 25 characters 131.2 bits Entering a passphrase I created using upper and lower case alphanumeric characters, with one special symbol character, and a total length of 24 characters generates an entropy value of 153.83 bits. If we add a couple of non-alphanumeric characters to the cartoon phrase, we get: correct-horse@battery-staple = 28 characters 172.19 bits The number of bits increase because the character set was increased in size, as well as the passphrase length. Now, if we plug in DarkDuck's example, we get: HYSYMBSITS = 10 characters 50 bits If we alternate upper and lower case, we get: HySyMbSiTs = 10 characters 58.83 bits That's a bit of an improvement, but the passphrase is much shorter than the XKCD example. So, if we take the first letter of each word from the first three lines of the song, Quoting:Have you seen your mother, baby, standing in the shadow? we get: hysymbsitshyhabsitsigioye = 25 characters 130.24 bits Same number of characters as in the XKCD example, and an entropy value which is just slightly less. The difference is that the cartoon example uses all dictionary words and DarkDuck's doesn't. It could make a difference if a cracker is using a dictionary based attack. There's a pretty good discussion on the ifs, buts, whys and wherefores here. |
| albinard Sep 20, 2013 12:42 PM EDT |
And if you extend the character list as in the example in the blog, you get up to a little over 62 bits. Not bad for remembering a single line of song! |
| BernardSwiss Sep 20, 2013 3:47 PM EDT |
“thereisnofatebutwhatwemake”—Turbo-charged cracking comes to long passwords http://arstechnica.com/security/2013/08/thereisnofatebutwhat... |
| kikinovak Sep 20, 2013 5:57 PM EDT |
$ pwgen -n -N 1 Keep it simple, stupid. |
| mbaehrlxer Sep 21, 2013 9:18 PM EDT |
from that pretty good discussion thread: Quoting:if you want to increase the total entropy in some scheme of choosing passwords, all other things being equal, you get more benefit from increasing n (length of the passphrase) than b (size of the character set). If you want to choose pronounceable passwords, it may be better to restrict yourself to an alphabetic character set (b = 52) and to increase n until you are above some threshold number of bits, bearing in mind that the entropy per character of natural language is typically about half that of completely random text. For this reason, a long passphrase which does not resemble a quotation from any published work may be preferable to a short password constructed using a large alphabet. is exactly the point xkcd is making. and i don't see anything in the other articles to contradict that. at best four words as xkcd suggests is not long enough. any password made up of initials of a list of words has less entropy than just using that list of words fully typed out. greetings, eMBee. |
| djohnston Sep 22, 2013 12:14 AM EDT |
eMBee,Quoting:any password made up of initials of a list of words has less entropy than just using that list of words fully typed out. I must be reading it incorrectly, then. Taking a portion of your quote from the thread on LinuxQuestions.org: Quoting:... bearing in mind that the entropy per character of natural language is typically about half that of completely random text. (emphasis added) Am I reading it the wrong way? Further down in the thread from Peufelon's quoted entry, H_TeXMeX_H says: Quoting:I think the most important thing in choosing a password is not to use dictionary words, these are easily cracked. I think the entropy of the RNG / seed is far more important than the password entropy. Hangdog42 answers that post with: Quoting:Absolutely. One other thing to avoid is l33tifying your passwords. I've recently seen some results from an SSH brute-force scanner and many of the passwords that are being tried are simply l33t v3rsions of dictionary words. I suspect the same sort of words are used in rainbow tables as well. Not using the "l33t v3rsions" of dictionary words was one of the points being made in the XKCD cartoon, I believe. Anyway, the disqualifier here is that I am not a cryptographic expert by any stretch of the imagination. I'm just looking at the math involved and whether it makes any sense. Greetings and salutations! |
| albinard Sep 22, 2013 11:57 AM EDT |
The password scheme I described in the article is based on the following reasoning: As djohnston noted, the entropy per character of natural language is typically about half that of completely random text. So it makes sense to start with random text. Where can one find random text that has any chance of being truly memorable? In the initial letters of a memorable phrase, poem, or song – the latter is especially subject to the “ear worm” phenomenon. So far, so good; but that just gives you letter text. If – repeat, IF – you could remember an encrypted version of that random letter text, you would open up the character set from an N of 26 to an N of 90 or more, depending on keyboard. When you type out the initial letters of the song, you use a keystroke for each letter as you recite it in your head. Okay, just do your same recitation, but choose in advance a different key for each word. It takes a few repetitions to firm up the sequence in your mind, but it creates a motor memory that will stay with you for a surprisingly long time. |
| mbaehrlxer Sep 22, 2013 9:58 PM EDT |
djohnston: what you may be missing is that the list of words fully typed out is much longer than a password made up of initials.
yes, for a single character using strange symbols increases your entropy. but if you use a word of several letter instead, you get more entropy still. if the length of your password is limited, then by all means go for those strange characters to increase your entropy, but otherwise, length wins. (and anyone forcing a limited password field should get insulted by linus) greetings, eMBee. |
| djohnston Sep 22, 2013 11:34 PM EDT |
Quoting:djohnston: what you may be missing is that the list of words fully typed out is much longer than a password made up of initials. yes, for a single character using strange symbols increases your entropy. but if you use a word of several letter instead, you get more entropy still. No, I understand that concept. |
| BernardSwiss Oct 09, 2013 2:15 AM EDT |
Pass-phrases and "obscure" long passwords are becoming less of a bulwark than they used to be. How the Bible and YouTube are fueling the next frontier of password cracking http://arstechnica.com/security/2013/10/how-the-bible-and-yo... (See also the article I referenced above...) |
| djohnston Oct 09, 2013 5:11 AM EDT |
Thanks for posting the link, Bernard. I have read the ArsTechnica article, as well as the one you posted previously. From the second ArsTechnica article,Quoting:For a graphic example of passphrase weakness, consider the string "Ph'nglui mglw'nafh Cthulhu R'lyeh wgah'nagl fhtagn1" (minus the quotes). With a length of 51 and a 95-character set containing upper- and lowercase letters, numbers, and special characters, its entropy is 284.9 bits. The total number of combinations required to brute-force crack it would be 95^51, making such a technique impossible on any sort of computer known to exist today. What's more, the string isn't found in any language dictionary. No wonder password strength meters like this one use words such as "overkill" to describe it. Both ArsTechnica articles describe the techniques used for a dictionary attack on a locally stored hash. I may be wrong, but I think you're missing the point albinard was making in his article. Yes, he is using a passphrase as a baseline. That is, he is using the words from a Rolling Stones song. But, his passphrase does not consist of the actual words. The passphrase is generated from the first letter of each word, which increases the entropy, (randomness or unpredictability), of the password. Generally speaking, using albinard's method, you will not find the password in any dictionary, collection of literary works or compilation of slang terms. As an example, let's take the phrase “I like to eat cake and ice cream, but not on Sundays because I may get my good clothes dirty". Using just the first letter of each word, preserving the capitalization, but omitting punctuation, we derive a passphrase of: IltecaicbnoSbImgmgcd Although the password is only 20 characters in length, I dare say you will not crack that “passphrase” with a dictionary attack as described in the ArsTechnica articles, regardless of how large the compiled dictionary is that is used. We could add a second phrase, such as “But I will eat cake and ice cream on any other day of the week”. The generated password, again only preserving capitalization, would then become: IltecaicbnoSbImgmgcdBIwecaicoaodotw That now gives us 35 characters for a password. The total number of combinations required to brute-force crack it would only be 52^35. We could increase that to 95^35 by including numbers and special characters, as in the "Ph'nglui mglw'nafh Cthulhu R'lyeh wgah'nagl fhtagn1" example. But, because the password does not match any known dictionary words or literary quotations, the entropy of the password has been increased beyond that of a standard passphrase, simply because it will not match any known language or literary patterns. Given massive computing power and an infinite amount of time, probably any password can eventually be cracked. But, I believe the method albinard describes is probably the best approach to use. |
| shem Oct 09, 2013 6:59 AM EDT |
@djohnston: But since that method is now published both here and in albinard's article, isn't one of the points that can be deduced from Ars' articles, that "they" will surely include a ruleset to check against that method? |
| gus3 Oct 09, 2013 2:05 PM EDT |
Only if you use those reference phrases to form the same passkey. |
| mbaehrlxer Oct 10, 2013 12:45 AM EDT |
gus3: which reference phrases?
if the algorithm generates phrases to try surely it can generate the abbreviation of them too. it would only double the number of tests. so you are better off using a phrase that can't be found in any text. in this sense both methods (using the full phrase, and using its abbreviation) are equal. the abbreviation can be found out trough testing pass phrases as well as brute force. but the long phrase can't be found through brute force (in sufficient time) so the phrase is still better. greetings, eMBee. |
| djohnston Oct 10, 2013 3:49 PM EDT |
Quoting:so you are better off using a phrase that can't be found in any text. in this sense both methods (using the full phrase, and using its abbreviation) are equal. By using a full phrase, even one you created, or a randomly generated haiku, you are including words and patterns that can be parsed from a dictionary. I'm beginning to see the wisdom of kikinovak's suggestion to simply use pwgen. The only drawback is the ability to associate and recall those random strings. Still, the generated passwords could be kept in a password manager, such as KeePass. |
| jdixon Oct 10, 2013 9:37 PM EDT |
> Still, the generated passwords could be kept in a password manager, such as KeePass. That seems to be the best long term solution, yes. A single good but memorable password to protect your password database, and a password manager to handle their usage. |
| gus3 Oct 12, 2013 10:20 AM EDT |
And a single point of failure to compromise all your passwords. |
| BernardSwiss Oct 12, 2013 10:25 PM EDT |
Some points covered here: Ars readers react to the wild west of password cracking http://arstechnica.com/tech-policy/2013/10/ars-readers-react... |
| djohnston Oct 12, 2013 10:38 PM EDT |
My head hurts. |
| jdixon Oct 13, 2013 9:02 AM EDT |
> And a single point of failure to compromise all your passwords. Yeo. There's always a tradeoff between security and convenience/usability. Each person/organization has to make that tradeoff decision for themselves. |
Posting in this forum is limited to members of the group: [ForumMods, SITEADMINS, MEMBERS.]
Becoming a member of LXer is easy and free. Join Us!
